Hello and welcome back to another Wi-Fi related blog post! This is part of a series of blog posts I’ve created following a lab setup that you can see here.
Today I’ll be talking about two well-known Wi-Fi based attacks. These attacks specifically target Wi-Fi Protected Setup (WPS) networks. In this post, I’ll be talking about how WPS works, tools, the types of attacks, and finally remediation.
So before I go into the nitty-gritty of WPS, I want to touch base with a little bit of history surrounding this protocol.
So WPS was introduced back in 2006 by Cisco as a way to allow non-technical users to authenticate into a Wi-Fi network without having to enter a complicated password and for smart devices like printers to connect. Skipping to a few years, two security researchers Stefan Viehböck (2011) and Dominique Bongard (2013) discovered huge flaws with this protocol where an attacker can crack the WPS PIN easily through brute forcing.
Tools to use
The tool that will be used in this post is:
How WPS Works
Before getting into the types of attacks, we need to understand how WPS works. Since the idea is to allow a user to authenticate easily into a Wi-Fi network, how is this authentication possible? WPS uses an 8 digit PIN, allowing authentication using this PIN.
WPS defines three types of devices on a network:
- Registrar - Device that permits or denies access to a network
- Enrollee - A device seeking to join the network
- AP - Access point that allows communication between the registrar and enrollee, some APs can function as both a registrar and AP.
Authentication using WPS has two primary modes: Push-Button-Connect (PBC) and PIN.
PBC
Users have to push a button, which can be virtual or physical, on both the AP and the wireless device. PBC on the AP is active for about 2 minutes before timing out. Knowing this, an attacker will need to have physical access to your AP or router.
PIN
PINs are usually available on the end sticker of a router/AP and must be entered either through internal or external registrars.
Internal registrars require a user to enter the PIN into a web interface of the AP. While external registrars require a user to enter the PIN of the AP into a form on the client device. We can see here that the most vulnerable would be the external registrar as our attack vector. This would mean that our attack method would be some kind of brute force attack to guess the PIN of the AP.
Extensible Access Protocol (EAP)
WPS uses both IEEE 802.11 and Extensible Authentication Protocol (EAP). EAP messages are exchanged, which consists of 8 in total with the first 2 being an exchange of public keys through DIffie-Hellman and the following then consists of proof that both the enrollee and registrar know the same PIN.
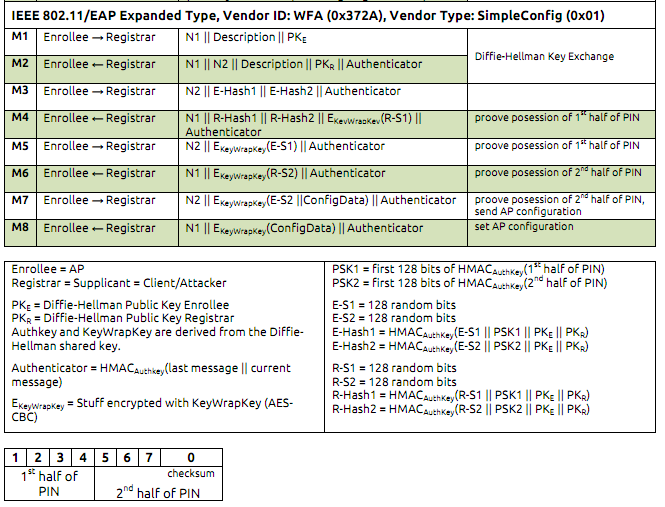
WPS Pin Attacks
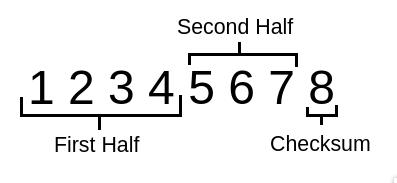
So knowing we can potentially brute force this pin, there’s 10 possibilities per digit and there’s 8 digits to form a PIN, that would imply 10 to the power 8 equaling 100 000 000 possibilities right? Well I wish, but unfortunately for vulnerable users (fortunate for the attacker) the pin is actually split into two, with the last digit in the pin just being the checksum.
How WPS Pin Attacks Work
Below we see how the PIN is split, the first half consisting of 4 digits implying 10^4 totalling 10000 possibilities and the second half being 3 digits implying 10^3 totalling 1000 possibilities. With this in mind, we only need to form 11000 possibilities to crack the PIN.
This means we would need to crack the first half of the pin and then the second half. What’s important to take out of this is how both the enrollee and the registrar react to this. IF the enrollee and the registrar detect that a part of the PIN is wrong, they will simply reply with a negative acknowledgement (NACK).
Going back to Figure 1 if a NACK is received after M4 that means the first part of the PIN is wrong, and after M6 implies that the second half is wrong.
Pixie Dust Attacks
A variation of the WPS brute force in which an attacker can gain the PIN through simply obtaining the nonces generated by an AP. These nonces are known as E-S1 and E-S2 and if the output is revealed, an attacker can use them to obtain the hash of the WPS PIN. One thing to keep in mind is that this is an offline attack.
Going back to figure 1, the most important part to keep in mind is M1, M2, and M3 for which we’re given:
- Diffie-Hellman public keys of both the enrollee and registrar
- Two hashes (E-Hash1 and E-Hash2) containing the WPS PIN halves (PSK1 and PSK2)
- Enrollee nonce and a derived auth key
Once we have these, we can attempt to brute force PSK1 and PSK2 after finding E-S1 and E-S2.
However, the most important thing to take away is that only certain routers from a number of vendors are vulnerable to this attack. This is because the nonces are supposedly randomly generated but aren’t for this vulnerability.
In some vendors such as Realtek the E-S1 and E-S2 nonces equate to the enrollee nonce or are derived from a UNIX timestamp or simply just a 0 like in Ralink or Mediatek router chipsets.
More information here. WiFi Router Database here.
Demo
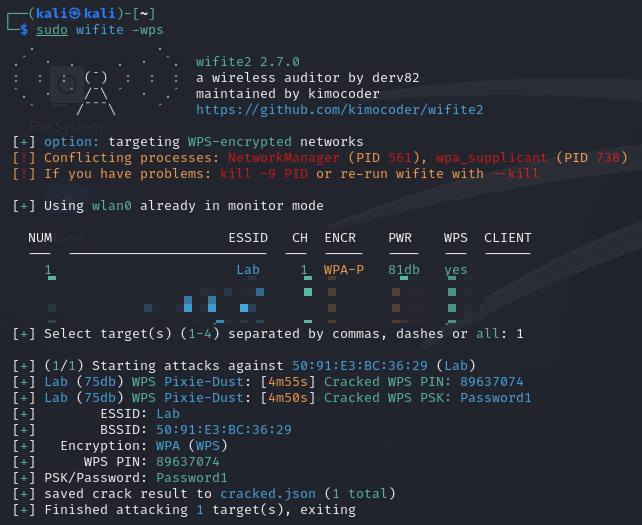
For this demo, I’ll be using the TP-Link Archer C50 which uses the MediaTek MT7628AN/MediaTek MT7612E chipset and is vulnerable to the pixie dust attack. The tool that will be run in this demo is wifite which is an automated script using the aircrack suite, reaver, and tshark.
We can actually just run one command since wifite will do everything for us from starting the adapter in monitor mode to cracking the pin:
sudo wifite --wps
Then we’ll choose our AP and let it conduct the Pixie Dust attack.
Manually using the aircrack suite and reaver:
sudo airmon-ng check kill
sudo airmon-ng start wlan0
sudo reaver -i wlan0 -b <mac-of-AP> -K -v
Remediation
So how do we defend from these types of attacks? WPS PIN brute forcing (online attack) is often non-existent nowadays, since modern day routers are often very good with implementing some form of lock out after 3-4 failed attempts at guessing the WPS PIN, the same can also be said for Pixie Dust attacks to an extent.
A lot of older routers however do not have these implementations, so it’s often best practice to disable WPS as a whole if the router supports the configuration.
Resources
WPS Vulnerable Routers https://docs.google.com/spreadsheets/d/1uJE5YYSP-wHUu5-smIMTmJNu84XAviw-yyTmHyVGmT0/edit#gid=0
Pixie Dust Vulnerable Routers https://docs.google.com/spreadsheets/d/1tSlbqVQ59kGn8hgmwcPTHUECQ3o9YhXR91A_p7Nnj5Y/edit?pref=2&pli=1#gid=2048815923
Stefan Viehböck’s paper on WPS Pin Attacks: https://www.cs.cmu.edu/~rdriley/330/papers/viehboeck_wps.pdf
Dominique Bongard’s PPT Presentation: http://archive.hack.lu/2014/Hacklu2014_offline_bruteforce_attack_on_wps.pdf
Offline WPS Pin Attack (Pixie Dust): https://forums.kali.org/showthread.php?24286-WPS-Pixie-Dust-Attack-(Offline-WPS-Attack)

